FIDO authentication protocols can be used as an alternative to passwords, and – in theory – they provide a fast and secure method for users to access online services requiring login credentials. However, FIDO authentication is not a magic bullet to defeat cybercrime and there are many considerations to take into account before paying over the top for FIDO-compatible solutions.
The Fast Identity Online (FIDO) Alliance was established in 2013 with the mission of reducing the “world´s over-reliance on passwords”. To help achieve its mission, the Alliance has developed a series of authentication protocols that resolve interoperability issues in technologies such as security tokens, biometrics, voice recognition software, and near field communications (NFCs).
The protocols enable users to register a FIDO authenticator (fingerprint reader, hardware key, TOTP service, etc.) with a compatible online service. Once registered, users can log into the website or app using the same authenticator without having to enter a username and password. In this respect, FIDO authentication saves users having to remember unique, complex passwords for each account.
The Security of FIDO Authentication
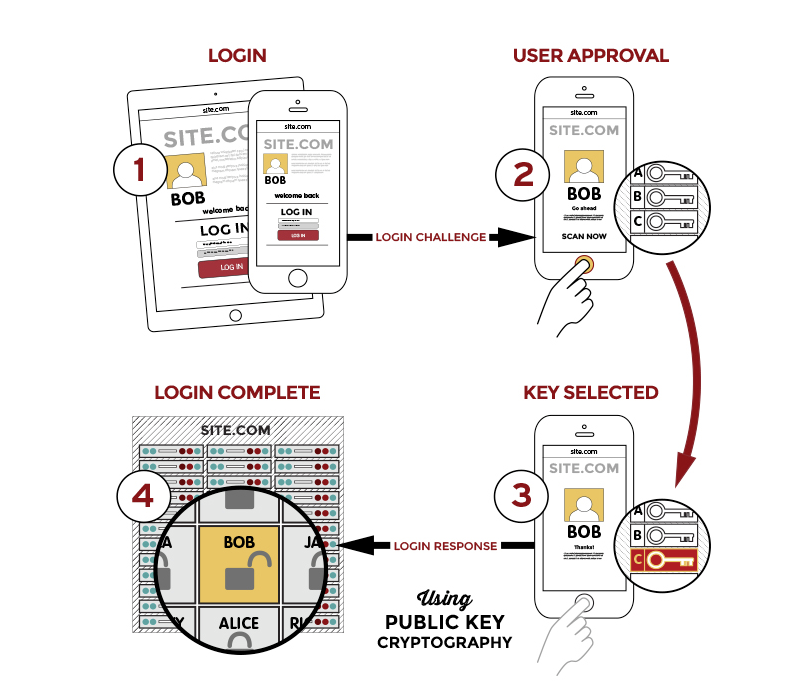
FIDO authentication protocols use standard public key cryptography techniques to create a key pair during the registration process. The device used during the registration process retains the private key, while the public key is registered with the online service. Then, during the login process, the device proves possession of the private key to the service by signing a challenge. Nether the private key, nor any information used to activate it (i.e., fingerprint), ever leaves the user´s device.
The FIDO authentication process significantly reduces the likelihood of unauthorized account access and data breaches attributable to lost, misused, and stolen login credentials. Furthermore, due to the way in which the private and public keys communicate with each other, the risk of falling victim to a phishing attack– even the latest transparent reverse proxy phishing attacks – is mitigated, while the protocols prevent all but the most sophisticated Man-in-the-Middle (MitM) attacks.
Consequently, with regards to the question “Is FIDO Authentication as Effective as It Claims to Be?” the answer is “almost” when you isolate the security element of the authentication process. However, technologies such as FIDO authentication protocols are only as effective as the people using the technologies and the processes put in place to enable people to use the technologies – and this is where the claims of FIDO being an effective authentication method hit bumps in the road.
The People and Processes Issues
The first – and probably the biggest – issue for businesses wanting to get away from unique, complex passwords for each account is that there can be a steep learning curve. Non-technical users might like the idea of (for example) voice recognition login but may find it difficult to understand how it works, establish that their device supports voice recognition software, download and configure FIDO-compatible software, and follow the FIDO authentication registration process.
Thereafter, further issues exist if authentication processes on unsecured devices are spoofed (you can´t replace a hacked voice ID like you can a hacked password), if devices are lost or stolen, or if a user records their voice in a quiet environment and then tries to log into an account in a noisy environment. Similarly, fingerprint scanners can get broken, hardware keys can stop working, and transactions between NFC-enabled devices and NFC readers can be corrupted.
Additionally, not that many online services support FIDO authentication (it´s taken long enough for some to support MFA!), you are not able to log into an online service unless you use an SSL/TLS encrypted Internet connection, and – if you use MFA alongside a FIDO authentication process – it adds another step to the login procedure compared to a password manager with autofill capabilities. For an individual security-conscious user, this may not be a deal-breaker; but, for a large business, the steep user learning curve and negative impact on productivity can be substantial over time.
The Days of Password Managers are Far from Gone
Because of the people and processes issues associated with FIDO authentication, the days of password managers are far from gone. Although the effectiveness of password managers is also dependent on how they are used and what processes are put in place to make sure they are used effectively, they have advantages over FIDO authentication methods inasmuch as password managers can be used to store and autofill other credentials such as credit cards and addresses.
That´s not to say that password managers are in direct competition with FIDO authentication processes. Many password manager providers support passwordless logins and several have joined the FIDO Alliance. Indeed, some password managers – i.e., Bitwarden – have already introduced capabilities to support FIDO authentication methods – enabling users to adopt passwordless logins while having the backup of a secure, cross-platform service in case of people and process issues.