Teleworkers are being targeted in a vishing campaign that has been active since mid-July, according to a recent joint security advisory issued by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA).
Vishing, or voice phishing as it is also known, is a form of phishing that occurs over the telephone. As with other forms of phishing, the aim is to get the victim to disclose sensitive information. In this case, the caller impersonates a trusted contact and uses social engineering techniques to convince a company employee to visit a fraudulent website where information is collected.
The attacks are targeted and prior to conducting the scam information is gathered on employees in the firm from social media networks such as LinkedIn. The social media sites are scraped to obtain personal information on employees such as their name, home address, personal telephone number, position in the company, and length of time they have worked at the firm.
A domain is registered using the format “company-support”, “support-company”, “employee-company”, “ticket-company”, and “company-okta” and a phishing form is loaded on the website. Employees are then contacted over the telephone with the caller impersonating the IT support team of their company or another legitimate individual in the firm using a VOIP number that spoofs the telephone number of a co-worker in the firm. The caller identifies themselves, uses the information gathered from social media networks to establish trust, and advises the employee they must login to a new VPN via a link sent to their phone.
They are told they must login and provide the 2FA code or one-time password sent to their phone. The link directs the employee to the fraudulent website, where their information is captured and used in real time on the genuine company VPN portal. When that login triggers a 2FA code, the employee, having been advised in advance, will then disclose that code which is also captured and used to grant corporate network access to the attacker.
In some cases, the attackers perform a SIM swap by contacting the employee’s mobile phone operator and porting the SIM to their own SIM card using the information gathered on social media sites for authentication. This ensures the 2FA code or OTP is sent directly to the scammer.
Once connected to the corporate network, sensitive data is stolen for use in other attacks and the VPN access is monetized.
Vishing attacks such as this are not new, but the move to teleworking due to the COVID-19 pandemic has increased the number of people working from home and accessing their corporate network through a VPN, which has made this attack much easier to perform.
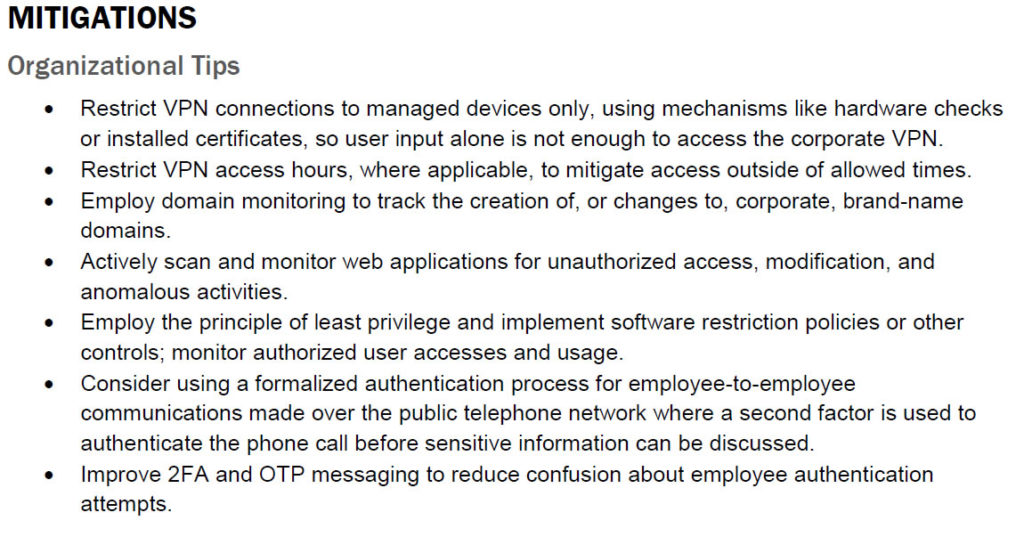
The FBI and CISA recommend organizations take the following steps to prevent attacks from succeeding: