How to Protect Against Phishing
Considering the volume of IT security articles published on the Internet, you might expect everyone would know how to protect against phishing. Right? Wrong. Phishing is the number one cyber-threat to individuals, small businesses and enterprise-scale networks; and, no matter which source of research you review, it is on the increase. Why? Because it works.
Phishing has evolved from the buckshot approach of sending millions of poorly-crafted spam emails to individually-targeted spear phishing campaigns. Although some phishing campaigns still focus on individual credit card fraud and identity theft, it has become more profitable for cyber-criminals to take over computer systems and networks in order to conduct illegal activities on a larger scale.
These illegal activities range from the distribution of malware and ransomware to cyber-jacking computers in order to install cryptocurrency mining software. Detecting these phishing campaigns has become harder due to the increased use of botnets and “nuisanceware” that have no user interaction. Consequently it is not only important individuals, small businesses and enterprise-scale networks know how to protect against phishing, but also how to detect and resolve phishing-related events.
Statistics about Phishing
Recent research conducted by the Anti-Phishing Working Group – a global coalition of law enforcement, government and industry leaders committed to fighting cybercrime – shows the threat from phishing is now greater than ever before.
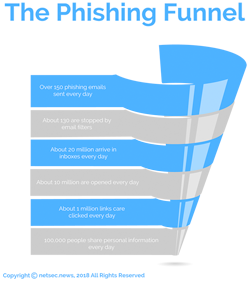
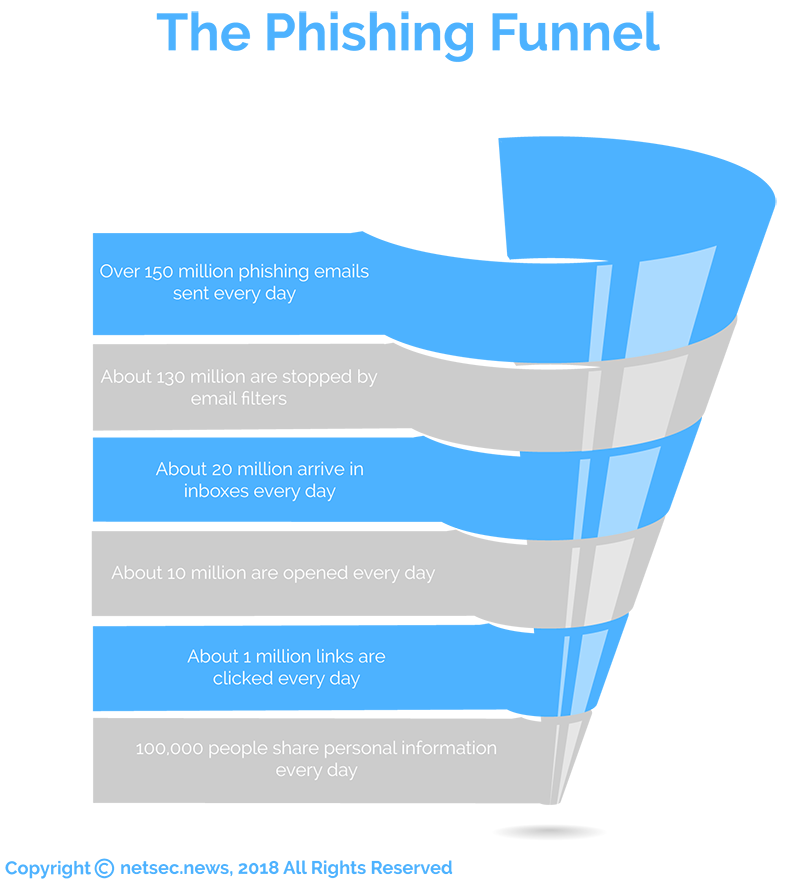
In 2016, 1,220,523 phishing attacks were reported, representing a 65% increase from the previous year. Research from the phishing defense solution provider Cofense (PhishMe) shows phishing attacks increased by 97.25% in Q3, 2016. Anti-phishing solution provider PhishLabs reported that phishing attacks on the five main targeted industry sectors increased by 33% in Q1, 2017.
Phishing emails are being used to obtain login credentials to email accounts and corporate networks, to spread malware infections, and install ransomware.
Cofense research shows 93% of all phishing emails are now used to spread ransomware.
Ransomware is a form of malware that encrypts files on the victim’s computer. The keys to unlock the encryption are offered in exchange for a sizeable ransom payment. In February 2017, Hollywood Presbyterian Medical Center was forced to pay a ransom demand of $17,000 to regain access to its files in addition to covering the cost from having its computer systems taken out of action for more than a week.
SamSam ransomware attacks on the healthcare industry typically see ransom demands issued of around $45,000. One healthcare organization, Hancock Health, paid a Bitcoin ransom of approximately $47,000 to recover its files.
The WannaCry ransomware attacks of 2016 saw more than 200,000 devices taken out of action across more than 150 countries. The UK’s National Health Service (NHS) was hit hard, with some NHS Trusts having computer systems taken out of action for more than a week.
Ransomware is a scourge that is causing havoc for businesses. IBM Security has reported damages from ransomware are likely to exceed $5 billion in 2017.
Ransom payments alone totaled more than $1 billion in 2016; however, the biggest losses come from computer downtime. One Providence law firm experienced 3 months of downtime as the result of a ransomware attack even though a ransom of $25,000 was paid. The associated loss in billings was in excess of $700,000.
Phishing attacks are often conducted to fool accounts department employees into making sizable bank transfers to criminals’ accounts – often for tens of thousands of dollars or more. Tripwire reports that, in 2016, one company lost $44 million as a result of a phishing scam.
While losses that large are something of a rarity, phishing-related data breaches often cost millions of dollars to resolve. The Ponemon Institute and IBM Security determined in 2017 that the average cost of a data breach was $3.62 million and phishing attacks have reportedly resulted in losses of $3.1 billion in 2016.
Cofense research indicates 91% of all data breaches start with a phishing email; and, with the volume of phishing attacks now being conducted, businesses must prepare and implement defenses that not only block phishing attacks but limit their severity when they do occur.
By adopting the right strategy, businesses can prevent phishing attacks and save millions of dollars each year.
Types of Phishing
| Phishing Technique | Attack Vector | Description |
| Phishing | Email/Internet | The broad term used to describe attacks that attempt to fool victims into disclosing sensitive information or installing malware. The scammer typically impersonates a brand, organization, or contact. |
| Spear Phishing | A targeted phishing attack on an individual, small group, or specific organization. Targets are researched and attacks are personalized. | |
| SMiShing | SMS and Instant Messaging Services | The use of SMS messages – or other messaging apps – to fool users into visiting a malicious website, installing malware, or making a call back. |
| Vishing | Telephone | Phishing attacks over the telephone, either speaking to a person or via automated voice response systems. |
| Whaling | A form of spear phishing targeting the CEO, CFO, or other high-ranking person in a company to gain access to their credentials. | |
| Pharming | A technique used to redirect Internet users to phishing websites, typically involving modification of DNS records. | |
| Business Email Compromise (BEC) / CEO Fraud | Typically, the second stage of a phishing attack, where phishing emails are sent internally via a compromised email account such as that of the CEO or CFO requesting data or wire transfers. |
Common Phishing Emails
Phishing can take many forms and cybercriminals are constantly changing their tactics so it is not possible to create a definitive lis; however, some of the most common types of phishing emails are listed below.
Typically, phishing attacks involve urgency – action must be taken quickly – and a threat – the consequences of failing to take a particular action.
| Phishing Example | Description | Target |
| Account Deactivation / Suspension | An issue has been detected with an account that requires immediate action to avoid account suspension/closure | All users |
| Fake Refunds | User is told they have a pending refund that requires confirmation of identity before it can be processed. | All users |
| Prize Wins | Users told they have won a prize or competition and need to make contact to collect their winnings | All users |
| Fake Orders / Invoices | Fake or missed invoices sent via email attachments or links to Google Docs/Dropbox. Primarily used to spread malware. | Businesses |
| Fake CVs | Responses to job advertisements and speculative approaches for work using CVs infected with malicious code. | HR Departments |
| Security Alert | Warning about a security issue on an account or a malware infection Often linked to tech support scams. | All users |
| Tech Support Scam | Email or popups warning of a malware infection or critical issue on a device. Requires a call to a help desk or the installation of fake AV software. | All users |
| HR Impersonation | Spoofed and compromised accounts used to send malicious message to employees from the HR department. | Employees |
| Data Requests | Requests by email, often from compromised email accounts, requesting data by email, such as copies of employee W-2 Forms. | Employees: Commonly HR, accounts, and payroll departments |
| Missed Delivery | Missed delivery notifications from a courier or logistics firm requiring a visit to a spoofed site or the opening of an email attachment containing malicious code. | All users |
| Account Information Confirmation | Email requesting confirmation of account details following a security breach. | All users |
| 419 Scams | Advance-fee fraud, taking its name from the law in Nigeria where many of the scams originate. A fee must be paid in order to receive a substantially larger amount. | All users |
| Law enforcement warnings | Notifications from police departments and the FBI warning of illegal activity that requires payment to resolve | All users |
| Legal scams | Subpoenas sent via email demanding appearance in court, with details included in a malicious attachment. | All users |
| SEO Poisoning | The use of search engine optimization techniques to get phishing websites appearing high in the search engine listings. | Internet users |
| Wire Transfer Scams | Requests to change bank account details of suppliers or for wire transfer payments to criminals’ accounts. Often uses compromised CEO/CFO email accounts. | Accounts and Payroll |
| Calls for Help | Fake pleas from friends, colleagues, and charities requesting urgent financial help. | All users |
How to Protect Against Phishing Attacks
Learning how to protect against phishing is essential, but unfortunately no single cybersecurity product will be effective at blocking all phishing attacks. That does not mean organizations cannot mount a highly effective defense against phishing, only that layered defenses are required, including technical and non-technical controls.
While there are many steps that can be taken to mitigate the threat from phishing attacks, two of the most important elements of phishing defenses are preventing phishing emails from being delivered to end users, and ensuring end users are trained to identify potentially malicious messages that make it past technological defenses.
Spam Filtering Software
One of the most important elements of any phishing defense strategy is to implement a spam email filtering solution. It is essential that email spam is filtered out to prevent as many phishing emails as possible from reaching employees´ inboxes.
Commercial spam filters use a variety of methods to distinguish genuine emails from spam and phishing emails. The combination of front-end tests and detection mechanisms means advanced spam filters can block more than 99.9% of spam emails.
Even though great advances have been made in the past few years, and spam filtering solutions are highly effective at blocking malicious messages, no technological solution can be 100% effective, 100% of the time.
Cybercriminals are constantly developing new techniques and can fool spam filters by compromising the email accounts of “trusted sources”. Simply adding a spam filter will not protect against phishing attacks all of the time.
Figures from Cisco Talos suggest there are now 400 billion spam emails being sent each day, with Radicati research suggesting an average employee receives 96 emails per day.
Even a spam filter that blocks 99.9% of spam emails may see each employee receive at least one spam email per day.
It is therefore essential that employees are prepared to deal with phishing emails when they arrive and are taught the skills that will allow them to identify phishing attempts.
Employees can be turned into a security asset and can help an organization protect against phishing attempts. Without appropriate training, it is probable employees will be fooled into installing malware, divulging their login credentials, or allowing their computers to be used as portals for conducting other illegal activities.
Security Awareness Training
Security awareness training. which is a way to protect against phishing attacks, is an essential element of any phishing defense strategy and should be mandatory for all employees that have corporate email accounts – from the lowest level workers to board members and the CEO.
Ongoing anti-phishing training is necessary as employees may be frequently tested by cyber-criminals in different and evolving ways. Training programs should cover the main cybersecurity threats, risky practices to avoid, industry best practices, and how to distinguish malicious emails from genuine messages.
Employees should be told never to open email attachments or click hyperlinks in emails from unknown senders, and never to disclose sensitive corporate information such as login information over email or the Internet.
End users should be informed of the scare tactics used by cybercriminals and given examples of social engineering techniques commonly used in phishing emails.
By training the workforce to adopt security best practices and teaching the skills required to identify phishing emails, employees will be less likely to be fooled by email scams.
Security awareness training should not be a one-time checkbox option whenever a new employee joins the company. Even an annual training session is no longer sufficient. Security awareness training should be a continuous process with regular refresher training sessions provided throughout the year, including alerts on the latest phishing threats and new social engineering methods used by phishers.
To protect against phishing attacks, organizations must try to develop a security culture where every employee stops to think before responding to any email or web request for information. Each email received should be treated as a potential threat.
In addition to training, employees should have their phishing identification skills put to the test in a safe environment. Phishing simulation platforms are invaluable in this regard. Research from Cofense shows organizations typically reduce susceptibility to phishing scams by up to 95% by conducting regular phishing simulations.
IT professionals often view employees as a weak link in the security chain. However, with training and phishing simulations, employees can be turned into security assets and can become a strong last line of defense, helping their organization better protect against phishing attacks.
Security awareness training can:
- Decrease susceptibility to phishing attacks by up to 95%
- Eradicate risky behavior that could lead to a data breach
- Help to develop a security culture where users are aware of common cybersecurity threats
- Teach employees to report suspicious activities to their security team
- Save time that would otherwise be spent responding to data breaches
- Save the considerable cost of mitigating a data breach
- Greatly improve an organization’s security posture
Implement a Mechanism that Allows End Users to Report Suspicious Emails
It is important to ensure all employees are trained and develop the necessary skills to identify potential phishing attacks, and that a mechanism is implemented that allows potentially suspicious emails to be reported to security teams.
If one end user receives a phishing email, the chances are that other individuals in the organization may have the same message delivered to their inboxes. One security-aware individual may recognize a phishing email, but others employees may not.
Implementing a one click reporting option, such as an Office 365 add-on, will allow an end user to mark a potential phishing email as suspicious and notify their security team.
The security team can monitor reported emails and take action to remove all copies of phishing emails from their organization’s email system.
Many anti-phishing vendors and security awareness training companies offer a one-click phishing email reporting solution that can be added to mail clients.
Multi-Factor Authentication
Multi-factor authentication, typically two-factor authentication, is an important security control that can help to prevent account access by unauthorized individuals.
Two-factor authentication requires the use of two methods of authenticating a user before access to an account is granted. The first form of authentication is something that an account holder knows, such as a password or passphrase. While that password or passphrase should never be disclosed or shared with anyone else, passwords can be obtained through phishing.
The second form of authentication is something an individual has – a token. That can be a hardware token, a device required to access an account such as a key fob or card reader – or it could be a previously authenticated device such as a mobile phone to which an access code is sent.
Two-factor authentication may not prevent unauthorized individuals from obtaining user credentials through phishing emails and websites, but it is an important security control that can protect against phishing by limiting the damage that can be caused by stolen user credentials.
Without the token/access code, cyber-criminals will not be able to access the account from an unrecognized device or IP address. However, if the authorized user´s device has been previously compromised by a botnet with command and control capabilities, two-factor authentication is not completely effective as cyber-criminals will have access to the account when the authorized user is logged in.
For this reason it is recommended further security mechanisms are implemented to protect against phishing – especially those that can prevent cyber-criminals infecting devices with botnets and cryptocurrency mining software.
Internet Filtering Controls
Phishing emails typically take one of three forms.
- A message could include an attachment that contains malware or malicious code that downloads a malicious payload.
- The message starts off a conversation between the recipient and the sender that ultimately leads to a request to disclose sensitive information, install malware, or perform an action such as making a fraudulent bank transfer.
- The message contains a hyperlink to a webpage hosting an exploit kit that probes for vulnerabilities, to a webpage already exploited to download malware, or a webpage that requests login credentials.
Internet filtering controls can help to protect against the latter and are an important control to protect against phishing attacks. Advanced web filtering solutions can be deployed which prevent end users clicking through from malicious links in phishing emails. At the most aggressive configuration, organizations can permit employees to only visit whitelisted websites – websites that have been assessed as malware-free and necessary for work duties.
Most web filtering solutions incorporate blacklists of webpages and IP addresses that are known to be used for phishing or malware distribution. Any attempt to visit a blacklisted site will be blocked. Advanced filtering solutions will prevent the downloading of suspicious files and will decrypt, inspect, and re-encrypt HTTPS/SSL traffic.
Security Information and Event Management (SIEM)
The purpose of many phishing emails is to gain a foothold in the network, allowing the attackers to move onto the next phase of their attack: Investigating the network and moving laterally to infect as many systems and endpoints as possible.
Security Information and Event Management (SIEM) tools help protect against phishing attacks by detecting unauthorized users as they explore the network. By monitoring network activity, atypical behavior can be detected – unusual requests and actions, or activities that exceed a certain threshold such has atypically high numbers of file name changes which could indicate a ransomware attack in progress.
SIEM tools will issue security alerts in real-time when events such as brute force attempts to guess passwords are in progress. The tools can also issue alerts about potential worm propagation, the presence of malware on a host, unusual port activity around the network perimeter, and excessive bandwidth use due to the presence of cryptocurrency mining software.
Threat Intelligence Services
To protect against phishing attacks, organizations need to be proactive. The tactics used by cyber-criminals often change. Signing up with a threat intelligence service will provide timely information on the latest threats, allowing organizations to take steps to block new tools, tactics, and procedures used by cyber-criminals. Being forewarned is being forearmed.
Threat intelligence services gather vast amounts of threat data, process that information, and translate it into actionable intelligence to guide security efforts. Many threat intelligence services feed data directly into security appliances and systems, send email alerts to security teams on pertinent threats.
These services allow organizations to stay ahead of the curve and better protect against phishing and other cyber threats, by informing them who is conducting attacks, what data threat actors are attempting to access, how they are gaining access to networks and data, and provide Indicators of Compromise (IoC) to allow attacks in progress to be detected.
Implement Policies and Procedures for Verifying Certain Requests
Policies and procedures should be implemented to reduce the potential for financial losses and the disclosure of sensitive data.
Spear phishing attacks are often conducted in order to gain access to email accounts of board members or the CEO. Those accounts can then be used to conduct further attacks on the organizations employees. These scams are known as Business Email Compromise (BEC) attacks.
Requests are sent from the compromised account to the HR department to obtain sensitive data on employees (W-2 Forms), or to convince payroll or accounts department employees to make fraudulent wire transfers.
Policies and procedures should be devised and implemented that require any request for sensitive data via email to be verified by phone or other means. Policies should be introduced that require any wire transfer request over a certain threshold to be verified by phone or in person before the transfer is made.
How to Protect against Phishing Botnets
A botnet is a network of compromised computers that can be remotely controlled by a cyber-criminal. Most commonly used to conduct Dedicated Denial of Service (DDoS) attacks, botnets can be also used to send spam emails and phishing emails from compromised email accounts. These spam emails and phishing emails evade detection by email filters because they originate from trusted accounts with good IP reputations and no previous reports of spam being recorded by RBL agencies.
Individual users and employees are more likely to open an email from an apparent trusted source and follow its instructions. This can be a particular problem for businesses if a phishing botnet is already installed on an employee´s computer via a malware download, as most email filters only scan emails entering and leaving the network and not those circulating internally – which in some businesses can account for up to 70% of email traffic.
The best way to protect against phishing botnets infecting a network is to prevent the malware from being downloaded. Internet content filters and emails filters with URIBL/SURBL filtering will help prevent users visiting websites harboring botnet downloads, but businesses should also implement mechanisms to prevent botnets being imported from mobile devices and removable USB drives when they connect with the business´s network.
The problem of phishing botnets should not be underestimated. In its 2017 Internet Security Threat Report, Symantec identified 98.6 million botnets in existence. Although not all of these were used for sending spam and phishing emails, McAfee reported in March 2018 that 97% of all the spam email sent in the last quarter of 2017 was attributable to just two massive botnets – “Necurs” and “Gamut”.
Cryptocurrency Mining Software and its Consequences
Several IT security companies have noted an increase in phishing emails harboring cryptocurrency mining software. Indeed one IT security company recently suggested cryptocurrency mining software could soon overtake ransomware as the malware payload of choice for cyber-criminals. The company´s reasoning was that cryptocurrency mining is expensive, and it is more profitable for cyber-criminals to infect other users´ networks and leverage their computer power and electricity.
The benefit for cyber-criminals is that few users realize their computer power is diminishing and their electricity costs are increasing – or, if the users do realize the changes, they attribute them to something other than cryptocurrency mining. This allows cyber-criminals to continue taking advantage of the host computers and remain undetected for long periods of time. In the long term, cryptocurrency mining software can be more profitable for cyber-criminals than ransomware.
Although the immediate consequences of cryptocurrency mining software are not as drastic as ransomware, the cost can be significantly higher over the long term for individuals, SMEs and enterprise-scale networks. For this reason, it is recommended to implement the measures suggested above to prevent the download of cryptocurrency mining software and to monitor network activity with a network monitoring tool.
Summary
Mounting an effective defense against phishing requires a combination of technologies, policies, procedures, and good security awareness.
The tactics of cybercriminals are constantly changing with new social engineering techniques, scams, and attack methods constantly being developed by threat actors to to bypass security controls and fool end users into disclosing credentials and installing malware.
It is possible to mount an effective defense to protect against phishing, but defenses need to be maintained and augmented over time. The organizations best protected against phishing are those that are proactive and take steps to mitigate emerging threats.
A continuous security awareness training and phishing simulation program should be implemented, threat intelligence should be gathered and used to tweak defenses, and cybersecurity solutions should be kept up to date and augmented whenever possible.
With layered defenses it is possible to protect against phishing and reduce the probability of a successful attack to a minimal level. Combined with intrusion detection solutions and a good incident response, disruption and losses can be kept to a bare minimum.