Phishing Examples
Security awareness training can prepare employees for phishing attacks, with phishing examples a good way of showing employees the main methods used by cybercriminals to obtain sensitive data or install malware.
Training should include phishing examples that highlight the common phishing email identifiers in order to teach employees how to determine if an email is genuine. Phishing examples can also be used to highlight the social engineering techniques commonly used in phishing emails.
It would not be possible to provide employees with phishing examples to cover all potential attacks, as cybercriminals are constantly changing tactics. However, by covering the main phishing email identifiers and providing phishing examples detailing the most common email types, organizations can greatly enhance their phishing defenses.
Phishing Examples Showing the Most Common Attack Types
Recent phishing examples have been detailed below to illustrate some of the methods used by cybercriminals to obtain login credentials, data and install malware.
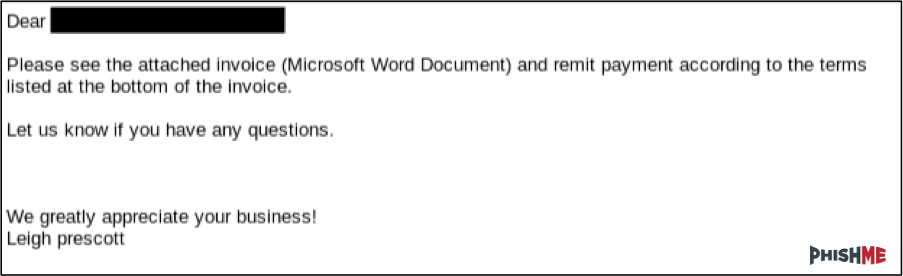
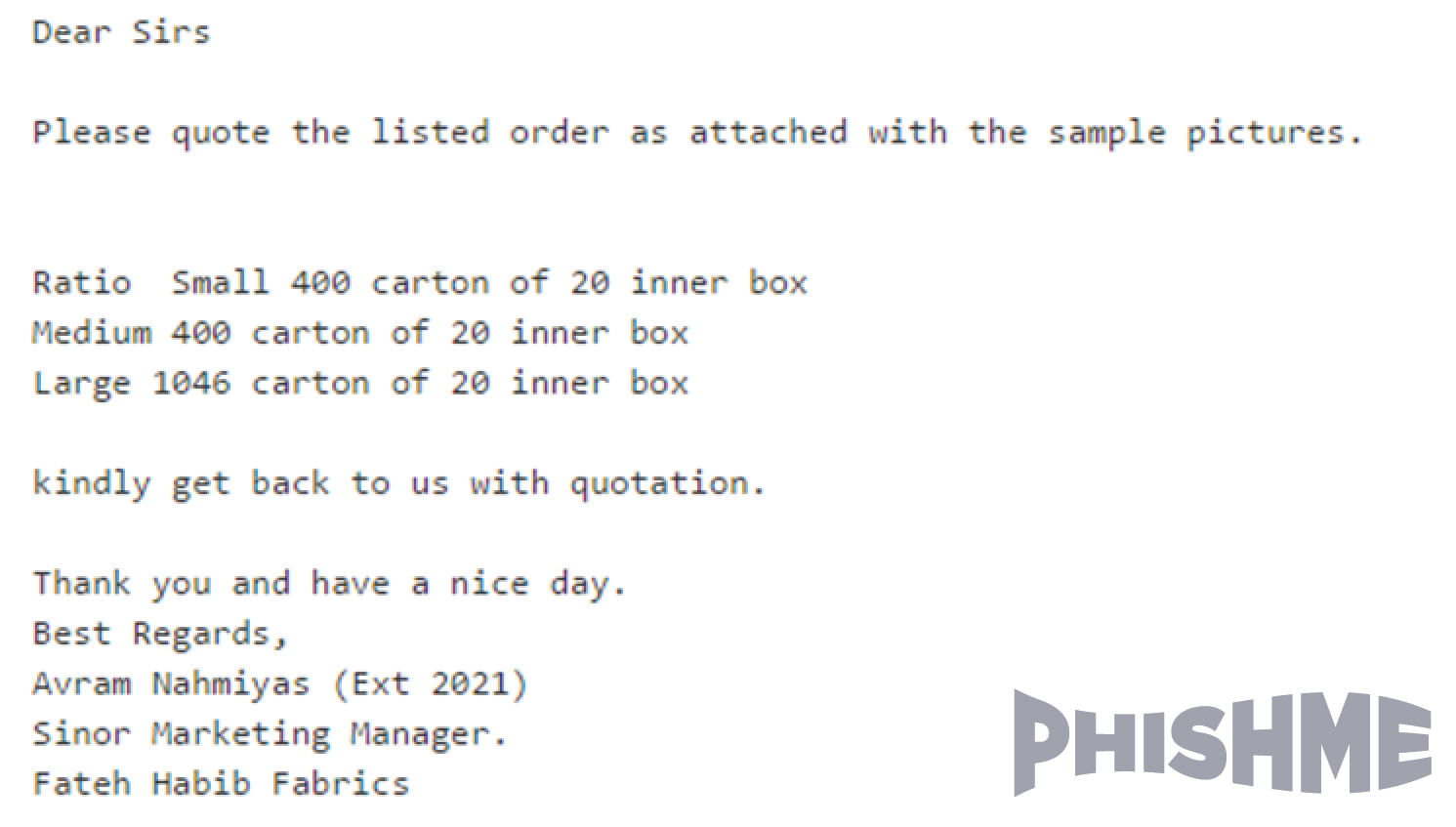
Fake Invoices and Purchase Orders
One of the commonest phishing scams involves sending a fake invoice or a purchase order. Invoices and purchase orders are commonly received via email and may not arouse suspicion. Malicious email attachments take many forms, with Microsoft Office Documents, HTML files and PDF files commonly used. The attachments contain malicious macros, JavaScript or VB scripts that download the malicious payload.
Security Alerts and Account Suspension
Scammers commonly add urgency to their emails and use scare tactics to convince end users that urgent action is required to secure their accounts and prevent imminent cyberattacks. Users are also threatened with account closures or loss of services if fast action is not taken to address an issue.
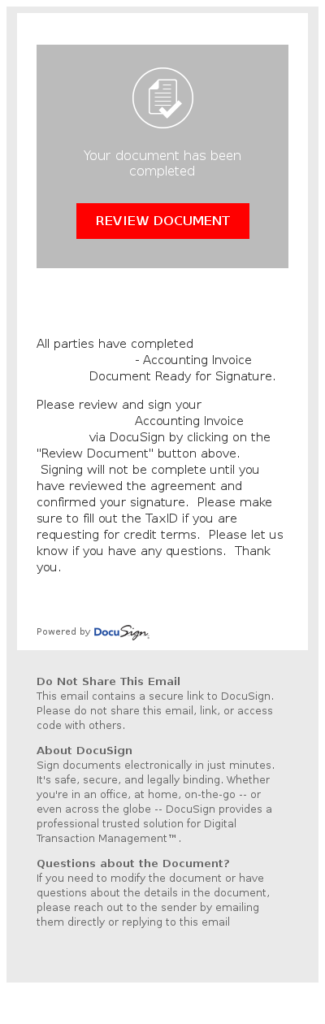
DocuSign Scam
DocuSign is used by organizations to review documents and obtain electronic signatures so it will be familiar to many employees. This scam involves an email that closely mimics official DocuSign emails. However, clicking the link will direct the user to a site that downloads DELoader financial malware.
Banking Institution Scams
Cybercriminals often create phishing emails mimicking those sent by financial institutions. A warning from a bank about a failed Direct Debit or missed payment is sure to get a quick response to prevent charges being applied. One such email scam was recently sent to Wells Fargo customers.
Business Email Compromise Scams
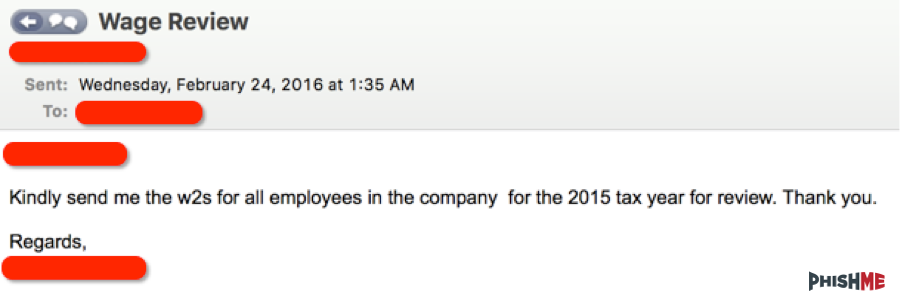
A popular business email compromise scam that has been seen extensively in 2017 involves a request for employees’ W-2 form data. The emails appear to have been sent from the CFO and request the W-2 Forms of all employees who have worked in the previous fiscal year. The emails are sent to specific individuals in the payroll or accounts department.
Business email compromise attacks commonly involve requests to transfer funds to the attackers’ accounts. New payment requests are made or requests made to change the bank details of existing suppliers. If a cybercriminal has access to the email account of the CEO or another C-suite executive, it is easy to identify existing suppliers and gather information on typical transfer amounts.
Send Phishing Examples to Employees Regularly
Security awareness training should be part of an employee’s induction when joining the company and training should be provided before an employee is given a corporate email account.
Phishing examples can help to improve understanding of the threats likely to be encountered; however, the tactics used by cybercriminals are constantly changing. Training will therefore not be effective if it is provided once. Training needs to be an ongoing process to ensure continuous protection.
IT security teams should keep abreast of the latest phishing threats and should send phishing examples to employees when a new, pertinent threat is discovered. These security bulletins reinforce training and alert employees to specific threats.
The Importance of Phishing Simulations
Interactive computer based training with phishing examples will help to raise security awareness and train employees how to identify phishing emails, although organizations will not know how effective their security awareness training has been until employees’ phishing identification skills have been put to the test.
Rather than wait for a phishing attack to occur to discover John in the marketing department wasn’t paying attention during training, organizations can conduct phishing simulations – real-world phishing attacks conducted in a safe environment.
Phishing simulation platforms allow IT security teams to schedule phishing emails to be sent to employees at random at different times of the day. Some solutions allow multiple phishing examples to be sent to the workforce simultaneously, each using different tricks and techniques that are currently being used in real world attacks.
Phishing simulations should include a wide range of scenarios, including click-only phishing emails containing hyperlinks, emails containing attachments, double-barreled attacks using emails and SMS messages, data entry attacks requiring users to enter login credentials and personalized spear phishing attacks.
Rather than infecting and end user with malware, when an end user falls for a simulation they can be informed of their error and the failure can be turned into a training opportunity. Administrators are also sent reports of the individuals that have failed a simulation to allow them to schedule additional training.
Phishing simulations are highly effective at reinforcing training and decrease susceptibility to phishing attacks. Figures from Wombat Security indicate phishing simulations can reduce susceptibility by up to 90%, while PhishMe’s simulations have been shown to reduce susceptibility by up to 95%.
Many simulation platforms also include a reporting function that lets employees report suspicious emails to their security teams with a single click, allowing rapid action to be taken to neutralize a threat.
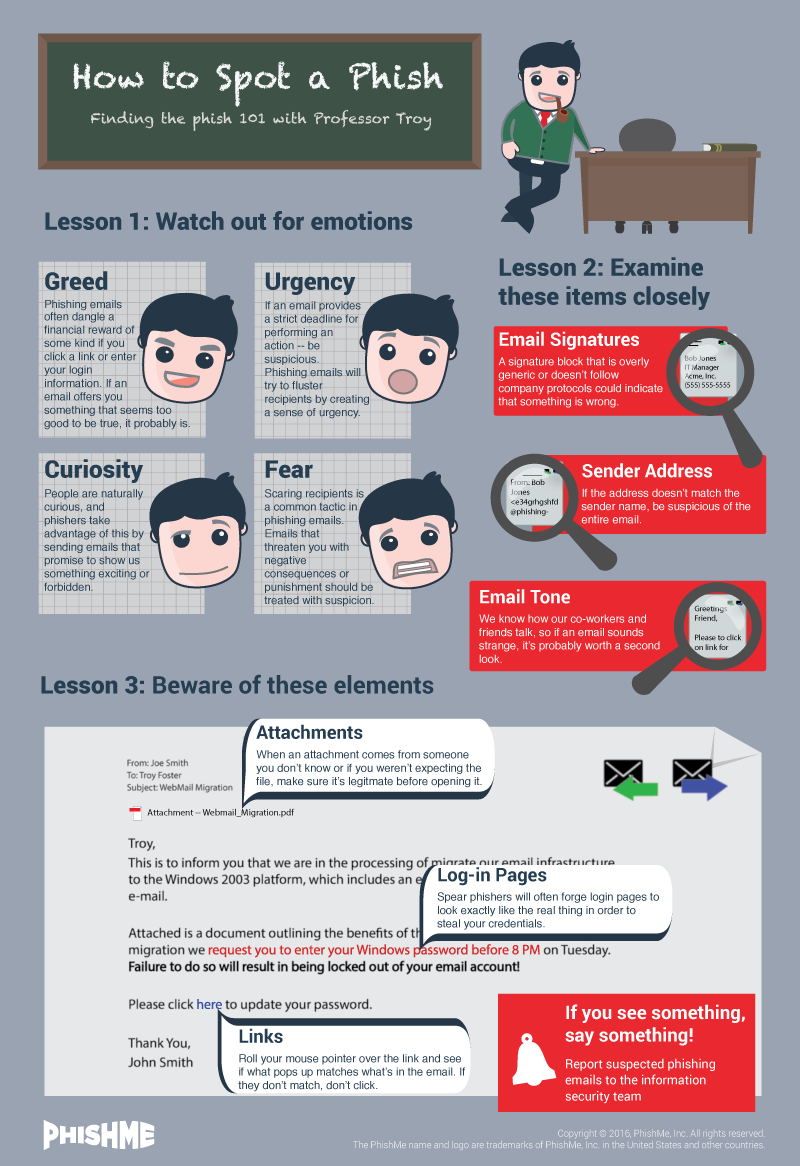
How to Identify a Phish
There are common tell-tale signs that an email is not genuine and is an attempt to obtain sensitive information or install malware. Some of the common identifiers of phishing emails have been summarized in the infographic below: