The digital communication platform provider Twilio has confirmed that multiple employees have been tricked into disclosing their account credentials in a smishing attack. Smishing is the use of SMS messages for conducting a phishing attack to steal employee credentials. Those credentials can be used to access employee accounts and any sensitive data accessible through those accounts.
Twilio provides programmable communication tools for making and receiving phone calls, sending and receiving text messages, and other communication functions, and the platform is used by many large companies for customer engagement, including Twitter, Uber, and Deliveroo.
Twilio detected suspicious activity in certain employee accounts on August 4, 2022, and traced the activity back to responses by the employees to SMS messages. Twilio said current and former employees had reported receiving SMS messages that appeared to have been sent by the IT department asking them to log in to change their passwords or to see updates to their Twilio schedules.
The messages included a link to click to perform the requested action. The URLs contained words such as Twilio, Okta, and SSO to make the recipients of the SMS messages think they were being directed to a legitimate website. The linked websites included a cloned version of the Twilio login prompt, and several employees proceeded to log in. Their credentials were then captured and used by the scammers to access their accounts. Twilio said the accounts contained some customer data, which may have been accessed or acquired. The investigation into the attack and data breach is still in the early stages and the company is working with the affected customers.
Twilio said the messages were sent through U.S. carrier networks and the company has been working with those companies to shut the campaign down. Twilio has also contacted the companies hosting the websites to get those sites taken down, but the scammers simply pivot to other carriers and websites to continue their campaign.
Twilio said this was a sophisticated social engineering attack in which the scammer had the ability to match employee names from sources with their phone numbers. The campaign targeted Twilio employees, but other companies have also reported similar attacks. The threat actors behind the attack have not been identified, but Twilio said that based on the findings of the investigation so far, they are well-organized, sophisticated, and methodical in their actions. Twilio said steps have been taken to improve employee awareness of social engineering attacks such as this and technical measures will be implemented to prevent further attacks.
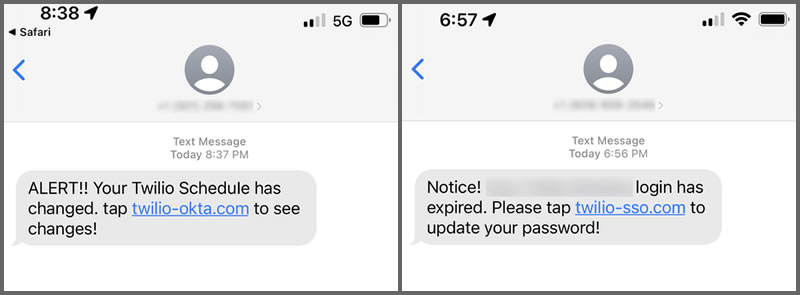
Examples of the SMS phishing messages received by Twilio employees. Source Twilio.
Smishing attacks are less common than email phishing, but attacks are increasing. The best defense against this type of phishing is security awareness training for the workforce. Employees should be trained how to recognize social engineering attacks, including phishing, smishing, and voice phishing. Through regular training and reinforcement, susceptibility to social engineering attacks can be greatly reduced. It is also recommended to implement multifactor authentication on accounts. If passwords are compromised, MFA can prevent the stolen credentials from being used to access accounts.
