The Russian Advanced Persistent Threat (APT) group Nobelium – aka APT29/The Dukes/Cozy Bear – that was behind the SolarWinds Orion supply chain attack has been conducting a spear phishing campaign masquerading as the U.S. Agency for International Development (USAID). The emails are used to deliver malware and gain persistent access to the internal networks of the targeted companies.
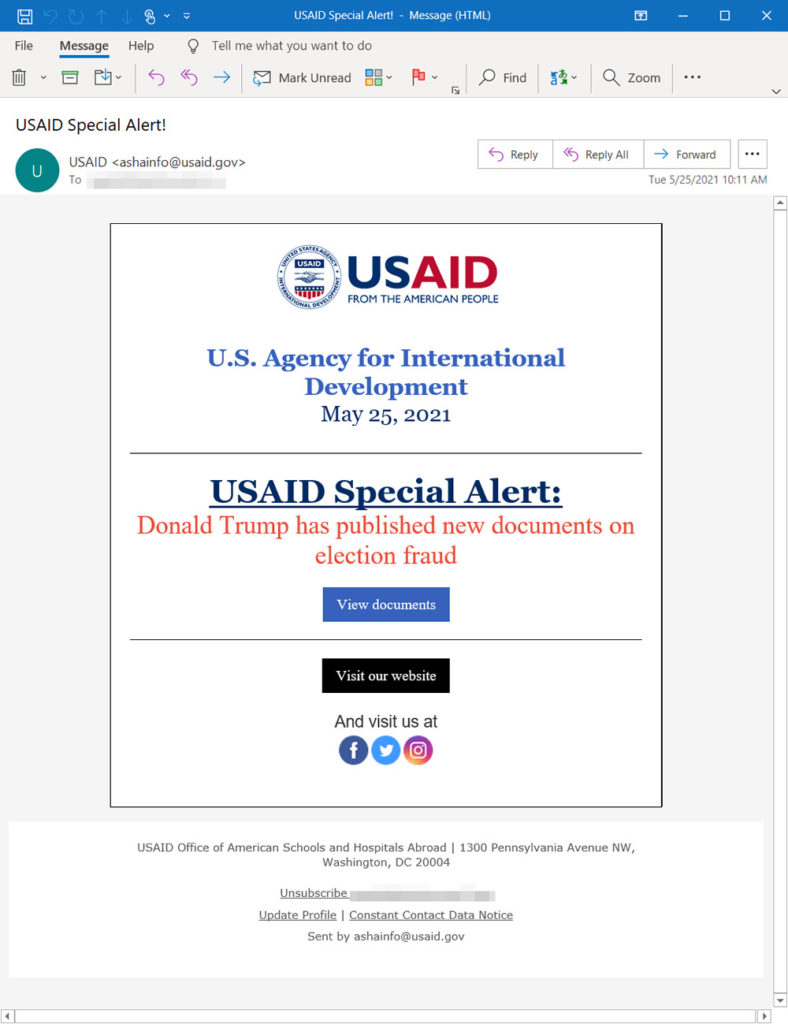
The spear phishing attacks were identified by the Microsoft Threat Intelligence Center (MSTIC), which has been tracking the group’s activity since January 2021. Over the past few months, Nobelium has been experimenting with the campaign and its tactics, techniques, and procedures have been evolving. Most recently, the group has been using HTML file attachments in its emails with malicious links to a legitimate site, which redirect to a URL where an ISO file is delivered.
The recipient is encouraged to open the file, which will deliver a shortcut file (LNK) which executes a DLL that will deliver a Cobalt Strike beacon and backdoor MSTIC has named NativeZone. This will give the attackers persistent access to the target’s network. Once access is gained, Nobelium can achieve further objectives such as the delivery of further malware payloads, lateral movement, and data exfiltration.
MSTIC observed Nobelium ramping up its campaign in May after the group compromised the Constant Contact account of USAID, which was used to mass-mail around 3,000 individual accounts across approximately 150 organizations. MSTIC reports that most of the emails in the campaign would likely be marked as spam, although it is likely that many were delivered to inboxes.
Source; Microsoft
The emails had a reply-to address on the usaid.gov domain and were sent from an email address that ended in @in.constantcontact.com, with the addresses varying for each target. Clicking the link in the email directed the user first to the Constant Contact service, then to a Nobelium-operated domain.
Constant Contact is aware of the hijacking of the USAID account, which has temporarily been disabled and the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have been investigating the campaign. The U.S. Department of Justice has announced that two domains used by Nobelium have now been seized. Both domains were used to receive exfiltrated data from victims and for communication with the malware delivered to victim networks.
“Upon a recipient clicking on a spear-phishing email’s hyperlink, the victim computer was directed to download malware from a sub-domain of theyardservice[.]com. Using that initial foothold, the actors then downloaded the Cobalt Strike tool to maintain persistent presence and possibly deploy additional tools or malware to the victim’s network,” according to the Department of Justice.
“It is anticipated that additional activity may be carried out by the group using an evolving set of tactics,” said the Microsoft 365 Defender Threat Intelligence Team, which suggested several mitigations to counter the threat.
