Analysts at email security firm INKY have identified a new phishing campaign that uses mathematical symbols in spoofed corporate logos in an attempt to fool email security solutions and ensure the phishing messages get delivered to inboxes.
Many AI-based anti-phishing solutions can detect brand impersonation attacks and reject or quarantine messages rather than delivering to inboxes. If a message looks like it is from a known brand, it is checked against artifacts associated with the brand such as URLs, domain names, and certificates.
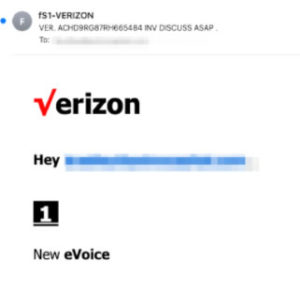
Doctored Verizon logo using square root symbol. Source: INKY
To circumvent these systems, the phishing campaign has incorporated various mathematical symbols, including the square root symbol, logical NOR operator, and checkmark symbol into the images. In one of the messages, a red square root symbol was used to replace the V in Verizon’s logo, which could be sufficient to fool email security solutions but is also sufficiently similar so that a user may not recognize the substitution in the logo has been made.
Three emails were detected by the researchers that used similar tactics, with all three using the same lure – a voicemail notification. In the message body of the email, an embedded “play” button is used, which links to a URL on the attacker’s domain. The landing pages similarly spoofed Verizon, although the cloned landing page uses the genuine rather than the doctored logo.
The landing page advises the user that they must enter their Office 365 account credentials in order to play the voicemail message. If the credentials are entered, the user will be advised that the incorrect password has been entered and they are prompted to attempt to log in again. This additional step is used to ensure that the incorrect password is not entered. On the second occasion, the user is informed, “Sorry but we are having trouble retrieving your files. Error (02992ACD9). A transient error has occurred. Please try again,” although recovery of a message will not be possible.
In this campaign, while the email message has the display name fS1-VERIZON, closer inspection reveals the email has not been sent from a Verizon domain. The landing page hosting the phishing content is similarly not on a Verizon domain. Instead, the attackers have used domains that have recently been purchased that have not yet been reported as malicious. Another red flag is accessing an authentic Verizon voicemail message does not require Microsoft Office 365 credentials to be entered.
