Researchers at Area 1 Security have identified a phishing scam that spoofs legitimate chemical companies, exporters and importers to deliver the Agent Tesla Remote Access Trojan (RAT).
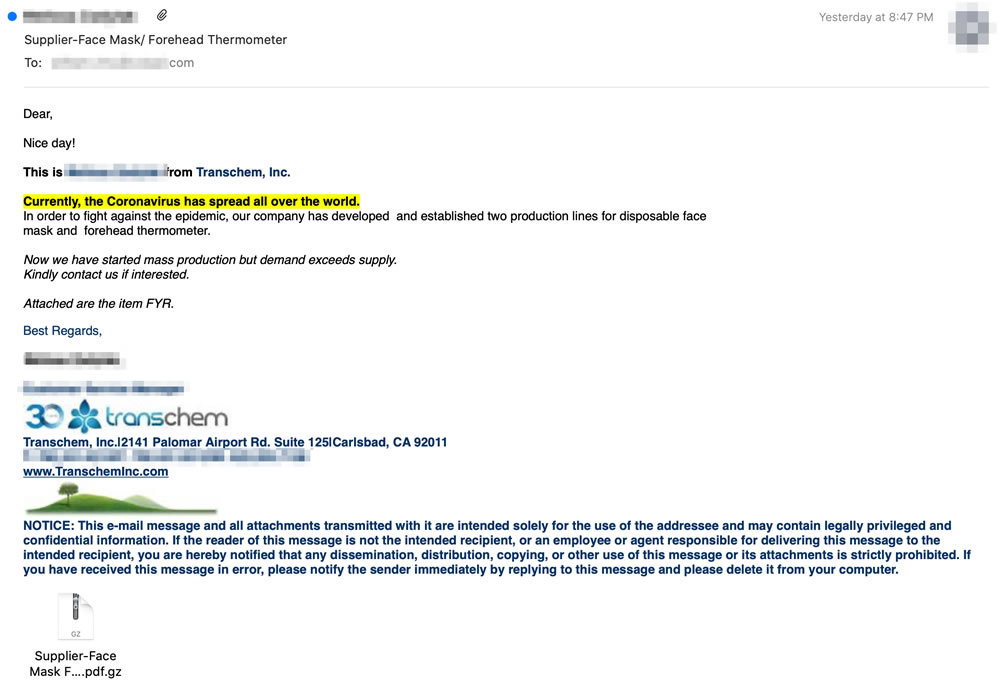
The phishing emails offer the recipient personal protective equipment (PPE) such as forehead temperature thermometers, disposable face masks, and other medical supplies that have been in short supply. The emails claim that the company has started mass producing PPE due to the shortages and advises the recipient that demand is exceeding supply.
The threat actors behind the campaign have gone the extra mile to make their emails appear legitimate. Several of the intercepted emails include the correct contact information for the company being spoofed, including the name of a real employee, contact information, and the correct company website. The emails also include the genuine company logo. The messages, at face value, appear legitimate.
Source: Area 1 Security
The emails include a compressed file attachment, which the recipient is asked to view. If the file is extracted, the user will be presented with what appears to be a PDF file; however, the file has a double extension and is really an executable file. In the default configuration, Windows will not display the (known) file extension, only displaying Supplier-Face Mask Forehead Thermometer.pdf.
If the user attempts to open the file, the Agent Tesla RAT will be installed. Agent Tesla is offered on hacking forums under the malware-as-service model. It is supplied with a user interface that tracks infections and to provide easy access to the information the RAT steals. The malware can be purchased cheaply, which has made It popular, although the researchers have found a torrent on Russian websites that provides the malware free of charge.
The Agent Tesla RAT is a keylogger and information stealer that can exfiltrate credentials from web browsers, email, FTP and VPN clients. The RAT can also steal data from the AppData folder. As a RAT, the malware can also allow users access to the infected device.
Several different companies have been impersonated as part of the malspam campaign, with the attackers taking advantage of misconfigurations of DMARC, DKIM, and SPF, which helps the emails to bypass anti-spam controls. The tactics, techniques, and procedures (TTPs) are also regularly changed, usually every 10 days. Tweaks are made to the email content and IP addresses are rotated to prevent the emails from being blocked by anti-spam solutions that are reliant on blacklists.
Antivirus engines used by anti-spam solutions may also fail to detect the malicious attachment, as for each wave of phishing emails the hash is changed, essentially transforming the Agent Tesla RAT into a new malware variant.
There have been some targeted attacks on large companies, including several Fortune 500 firms; but a shotgun approach appears to be favored.
Due to the changing TTPs, emails may not be detected by many antispam and anti-malware solutions. It is therefore advisable to alert employees about the campaign and to instruct them never to open email attachments in unsolicited messages and to be extra cautious about any email received related to COVID-19 or PPE.
