PhishLabs has identified an ongoing phishing campaign targeting Office 365 administrators. The aim of the campaign is to obtain Office 365 admin credentials.
Phishers face several challenges. Their own domains are likely to have a low trust score, which makes it easy for antispam solutions to identify their messages as malicious. To get around this issue, they need to obtain the credentials for a legitimate email account on a clean domain. I.e. one that has not been used for sending spam, phishing emails, or malware in the past.
If the domain has a good track record of being used to send benign messages, spam filtering solutions that assess messages based on the trust score of a domain are less likely to block the messages. That means the email account can be used for longer and more phishing emails will be delivered to inboxes.
If a standard Office 365 user’s email credentials are obtained, that account can be used to send phishing emails, but that is not ideal. The legitimate user of that account may notice the thousands of emails in their sent folder. Not all phishing emails will be sent to valid email accounts, so there are likely to be many failed delivery attempts and those messages will be delivered to the user’s inbox and will be noticed. The password will then be changed, and the phisher will be locked out of the account.
If an administrator account is compromised, it can be used to set up new accounts on the domain. They can then be used to send phishing emails. Since only the phisher will be using the new account, it is less likely that the malicious activity will be identified.
Admin accounts may also allow an attacker to obtain emails from all accounts in the Office 365 environment or take over those accounts. Email accounts contain a treasure trove of data that can be used for all manner of nefarious purposes. Office 365 administrators often have admin access to other systems. Once their account is compromised, password resets can be performed on those systems, and the attacker can gain access to far more than just the Office 365 environment.
The lures used in this campaign are varied, although the most common relate to invoices, where the user must sign into their Office 365 account to view the latest Microsoft invoice. Some messages state that the user’s Office 365 account has been placed on hold an action is required to unblock the account.
In all cases, a hyperlink is included in the email that directs the user to a cloned Office 365 login page on an attacker-controlled domain. If credentials are entered, they are captured by the attacker.
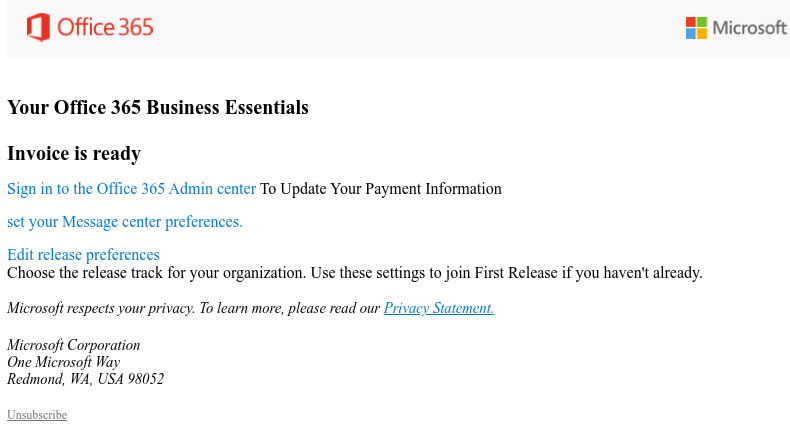
Image Source: PhishLabs
