Microsoft has announced it has taken steps to disrupt phishing campaigns conducted by a Russia-linked threat actor tracked as SEABORGIUM. The threat actor originates from Russia and conducts operations closely aligned with Russian interests. The threat group has been in operation since at least 2017, and the group is known to conduct phishing and credential theft campaigns, mostly targeting organizations in the United States and the United Kingdom, and to a much lesser extent, in the Baltic states, Nordics, and Eastern Europe. Microsoft said that in the months leading up to the invasion of Ukraine and beyond, the country has also been targeted; however, Ukraine is not believed to be a primary target. The group appears to be focused on espionage, which suggests the group is acting under the direction of a nation-state.
Phishing is used to gain access to victims’ networks for data theft. In some cases, data has been leaked after attacks to shape narratives in targeted countries. Victims include government organizations, NGOs, think tanks, former intelligence officials, and higher education institutions. The latest campaign conducted by the group has seen more than 30 accounts/organizations compromised this year.
Microsoft said the threat actor is highly persistent and individuals in an organization are subject to multiple attempts to compromise their accounts over a long period of time. Once a foothold has been gained in the network of a targeted organization, efforts are made to broaden the infiltration and compromise social networks through constant impersonation.
Over the past 5 years, the tactics and methodologies employed by the group have changed little. Microsoft notes that before an organization is targeted, extensive reconnaissance is conducted on targeted individuals to identify legitimate contacts that can be impersonated, and social media platforms, personal directories, and general open-source intelligence (OSINT) are used to supplement the reconnaissance efforts.
When contacts have been established, email accounts are set up with consumer email providers using their names, and those accounts are used to send phishing emails. Oftentimes, the initial contact involves a benign email to establish communication. In that conversation, an attachment is referenced that is not included in the email. If the target responds, a weaponized email is sent.
In another approach, the threat actor impersonates a leader in the targeted organization and sends a spear phishing email to selected individuals in that organization such as the message below.
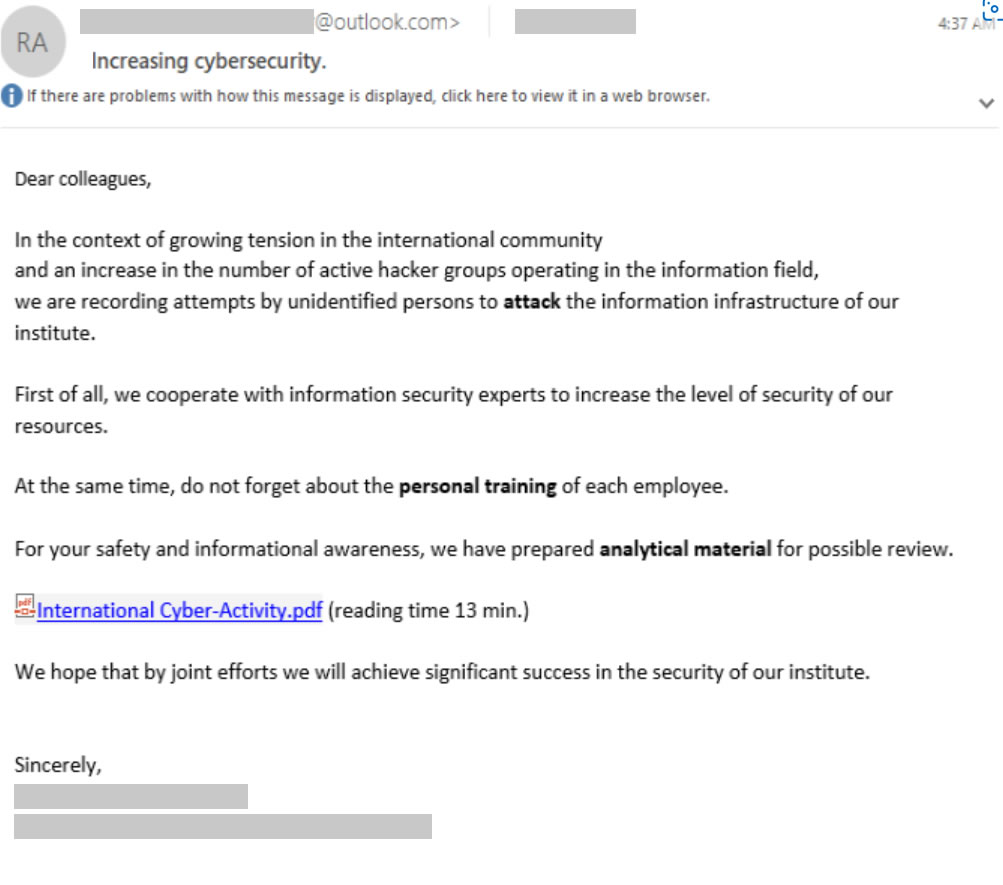
Examples of spear phishing emails sent by SEABORGIUM. Source: Microsoft.
Malicious links are embedded in emails and PDF attachments have been used that contain links to URLs, including shared files on OneDrive. Ultimately, the aim is to build a rapport and get the targeted individual to visit a web page that requests login credentials. Credentials for email accounts are obtained and emails are exfiltrated, forwarding rules are set up for persistent data collection, and the accounts are used for further internal phishing campaigns.
Microsoft has taken steps to disrupt the campaign through its security products (Microsoft Defender for Office 365, Microsoft 365 Defender, and Microsoft Defender SmartScreen) and has been working closely with the Google Threat Analysis Group (TAG) and the Proofpoint Threat Research Team to further disrupt operations.
Microsoft has shared Indicators of Compromise (IoCs) and recommended mitigations to help network defenders detect and block attacks.
