Microsoft has discovered a major phishing-as-a-service operation that it says is behind many phishing attacks on businesses over the past 3 years.
Phishing is one of the easiest ways for cybercriminals to gain access to business networks. Attackers require a phishing email template to use, need to have a domain to send emails, and a webpage where credentials are harvested. Creating the infrastructure to support phishing campaigns can be time consuming however, and once phishing campaigns are detected, the email addresses and domains will be blacklisted and will be blocked by security solutions such as spam filters and web filters.
Would be phishers often take advantage of phishing kits, which are offered on hacking forums. They make a one-time payment and are provided with the email templates and site templates for conducting their attacks. Phishing-as-a-service -PhaaS – operations make phishing even easier and provide a much broader range of services.
The BulletProofLink PhaaS operation detected by Microsoft significantly lowers the bar for conducting phishing attacks and makes conducting phishing attacks almost effortless. BulletProofLink is a full-service operation. Anyone wanting to conduct a phishing campaign can pay a weekly, biweekly, monthly, or annual subscription and all the tools are provided to allow phishing campaigns to be conducted. The cost ranges from about $50 for a single campaign up to around $800 for a monthly subscription.
Phishing as a Service vs Phishing Kits. Source: Microsoft
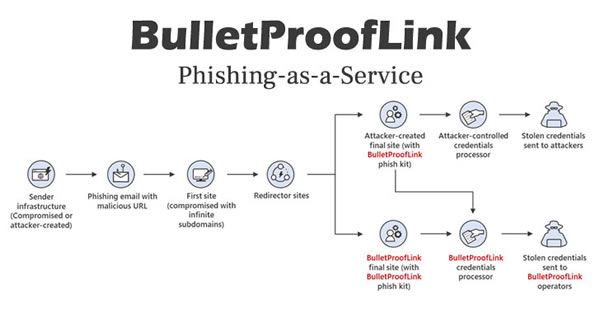
Microsoft said it was alerted to the operation, which has been running since at least 2018, while investigating a phishing attack. Microsoft said the campaign involved more than 300,000 subdomains, which suggested a phishing kit was involved. Further analysis allowed the Microsoft 365 Defender Threat Intelligence team to gain a comprehensive insight into the operation.
“An interesting aspect of the campaign that drew our attention was its use of a technique we call ‘infinite subdomain abuse,’ which happens when attackers compromise a website’s DNS or when a compromised site is configured with a DNS that allows wildcard subdomains,” said Microsoft. “Infinite subdomains allow attackers to use a unique URL for each recipient while only having to purchase or compromise one domain for weeks on end.”
Phishing templates. Source: Microsoft
The use of infinite subdomains is becoming much more common, as it means attackers do not need to obtain hundreds of single-use domains for use in attacks. It also allows them to easily create huge numbers of phishing URLs which makes it hard for security solutions that rely on exact matches of URLs to block attacks. This method allows phishers to create an infinite number of subdomains as a prefix to the base domain for each email.
The BulletProofLink PhaaS operation is run like a legitimate business. The operators have instructional videos on YouTube and Vimeo demonstrating how campaigns can be conducted. There is chat support through Skype, ICQ, forums, and chat rooms to help subscribers that encounter problems, and the operators of the PhaaS provide a 10% discount for any new customer. The PhaaS even has an online store where customers can register, sign in, and advertise their hosted service for a monthly subscription.
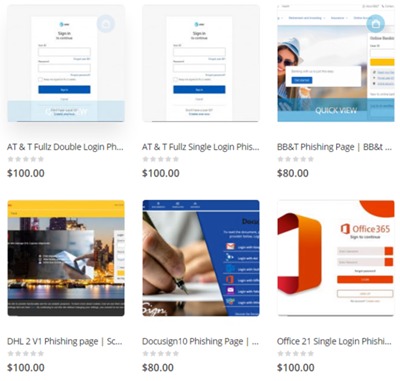
There are over 100 phishing email templates offered to subscribers to allow them to conduct campaigns targeting businesses or individuals. Those email templates include well-known company logos and impersonate many different brands and have fully undetected (FUD) links to help the messages evade security solutions. Subscribers just choose the template, send the emails, and collect the stolen credentials.
However, as is common with phishing kits and PhaaS operations, code has been included which allows the operators to obtain all credentials that are collected by subscribers. That means that in addition to the monthly subscription, they can also sell the credentials to other cybercriminal gangs as initial access brokers (IABs). Many ransomware gangs actively recruit IABs that can provide credentials for use in ransomware attacks, and that could well be where the real money is made by the gang.
