This week, Microsoft shared details of a massive phishing campaign that has targeted more than 10,000 organizations since September 2021. The campaign targets organizations that use Office 365 and allows the attackers to hijack accounts, even if they have multi-factor authentication (MFA) enabled. The compromised accounts are then used to conduct business email compromise attacks on external companies to get them to make fraudulent wire transfers to attacker-controlled bank accounts.
It is now a standard security practice to enable MFA on accounts. With MFA enabled, if a password is stolen – in a phishing attack for example – access to the account will not be granted unless an additional authentication factor is provided. This is typically a token, one-time code, fingerprint, or physical security key. While MFA greatly improves security – MFA blocks 99% of automated attacks on accounts according to Microsoft – it is not infallible, and this campaign allows MFA to be bypassed.
The emails direct users to a spoofed Microsoft page where the user is asked to enter their Office 365 credentials to log in. The intercepted emails use an HTML attachment to direct the user to the fake login page. Credentials are harvested on the site along with session cookies, in what is known as an adversary-in-the-middle (AiTM) attack, which allows the attacker to authenticate.
Once access is gained to the email account, the attacker reads emails, identifies potential targets for BEC attacks, sets up mailbox rules for incoming messages, and emails are crafted targeting companies to trick them into making large wire transfers. Since genuine message threads are used the emails are realistic and convincing, and the targeted company employee is likely to believe that they are communicating with the genuine account holder. Scams such as this could easily be identified by the genuine account holder, so rules are set up in the mailbox to mark certain messages as read and send them to the archive folder so they cannot easily be viewed. The attacker then logs in to the mailbox periodically to check messages
This campaign involves an attacker-controlled proxy site that sits between the targeted users and the work server they are attempting to log in to. The phishing sites use open-source phishing kits such as Evilginx2 and Muraena. When the username and password are entered, they are relayed to the genuine server, and the response from that server is then relayed to the targeted user. The authentication process is completed, and the session cookie is stolen from the legitimate server and is used to authenticate to Outlook online. This method works even if MFA is enabled.
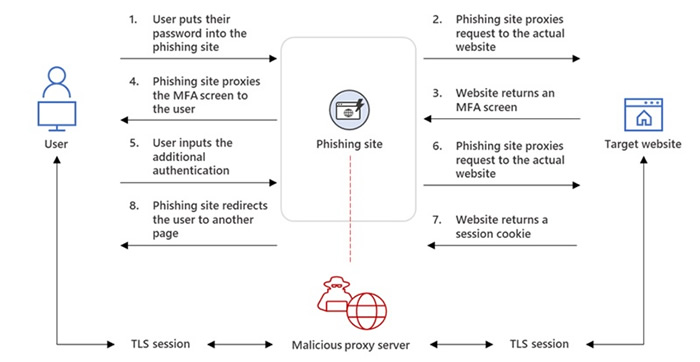
Source: Microsoft
Many businesses believe that MFA protects them against scams such as this, but that is not always the case. Microsoft recommends using making their MFA implementation “phish-resistant” by using solutions that support Fast ID Online (FIDO) v2.0 and certificate-based authentication. Additionally, conditional access policies should be enabled, advanced anti-phishing solutions used, and Microsoft also recommends continuously monitoring for suspicious or anomalous activities, such as odd sign-in attempts.
