Researchers at Fortinet’s FortiGuard Labs have identified a new spear phishing campaign that impersonates the World Health Organization (WHO) to distribute the LokiBot information stealer.
The emails incorporate the WHO logo and claim to offer important advice about COVID-19 infection control and give recommendations. The email states that the information in the email attachment is intended to address misinformation about the 2019 Novel Coronavirus and COVID-19.
Initially the campaign saw malspam emails sent to targets in Turkey, Germany, Austria, Portugal, and the United States, but the campaign has since been extended and emails have been sent to targets in Canada, Italy, Puerto Rico, Spain, and Belgium, albeit to a lesser degree.
As with several of the other COVID-19 campaigns impersonating WHO, the emails contain some spelling errors and grammatical mistakes which suggests that English may not be the first language of the scammers. The emails also refer to the Centre for Disease Control (CDC) at the World Health Organization, mixing both the U.S. Centers for Disease Control and Prevention with WHO, and also using the British spelling of ‘centre’ rather than the American spelling, center.
The emails intercepted by FortiGuard included an attachment titled COVID_19- WORLD HEALTH ORGANIZATION CDC_DOC.zip.arj, with the unusual file extension potentially used in an effort to fool recipients into thinking the file is not malicious. .arj files are compressed files, which can be opened with 7-Zip.
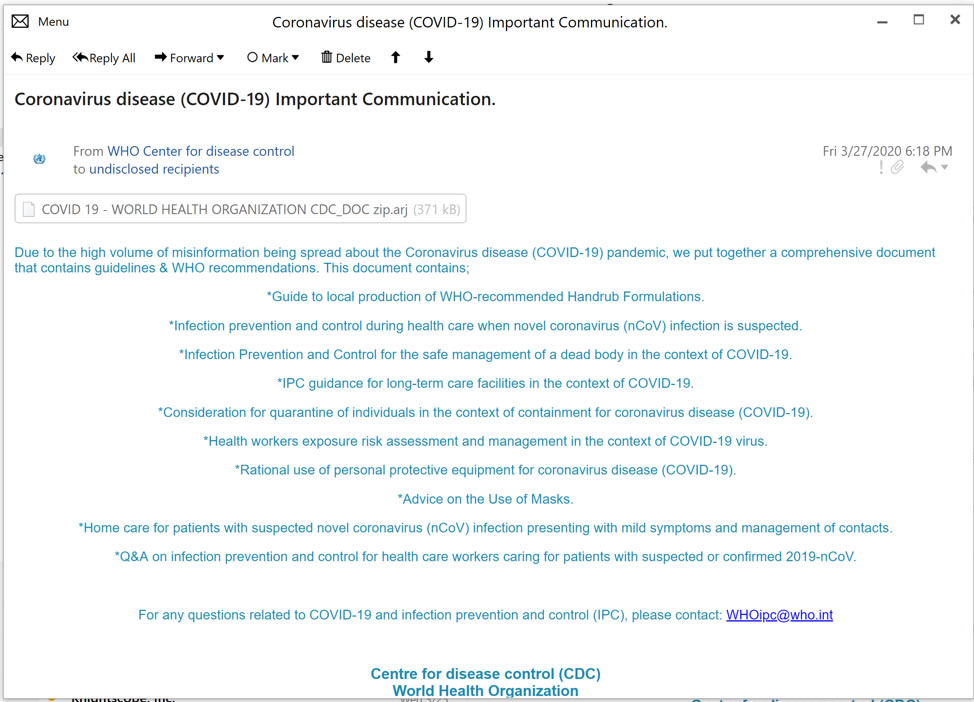
Spear phishing email impersonating WHO to spread the Lokibot Trojan. Source: FortiGuard Labs
If the file is decompressed, users will be able to open a file named DOC.pdf.exe. This is naturally an executable file, although the naming of the file may fool some people into thinking the file is harmless. Running that file will result in the downloading of the Lokibot information stealer.
Lokibot is a relatively simple Trojan malware that is used to steal a range of sensitive information such passwords stored in browsers and FTP credentials. The Trojan has previously been offered for sale on hacking forums and darknet marketplaces.
