A spam email campaign involving at least 100,000 emails has been conducted using ‘hacked’ FBI-owned servers. The messages advised the recipients that their network had been breached and data was stolen.
The emails were sent from the legitimate [email protected] email account and, as such, were passed by the DomainKeys Identified Mail (DKIM) mechanism. The Spamhaus project said the messages were delivered to at least 100,000 mailboxes, although it is possible the campaign was far larger. The emails appear to have been sent as a prank, rather than as part of a malicious campaign; however, a malicious campaign could have easily been conducted.
The FBI issued a statement about the email campaign and confirmed the messages falsely warned about a cyberattack, and that the messages were sent from infrastructure owned by the FBI and Department of Homeland Security. The messages were sent in two waves on Saturday morning around 5 a.m. UTC and 7 a.m. (UTC), with the recipients scraped from the American Registry for Internet Numbers (ARIN) database.
The issue exploited by the pranksters was a software configuration issue on the Law Enforcement Enterprise Portal (LEEP). The portal is used by federal, state, and local agencies for sharing information. The system includes a Virtual Command Center, which allows law enforcement to rapidly share real-time information about time-critical issues such as shootings.
The FBI confirmed that neither the FBI nor the DHS networks were compromised, and no sensitive data or personally identifiable information was obtained or viewed. Once the FBI was alerted, the software vulnerability was quickly mitigated and the FBI warned partners to ignore the fake emails.
The spam messages had the subject: “Urgent: Threat Actor in Systems.” According to Spamhaus, the emails had the following text in the message body:
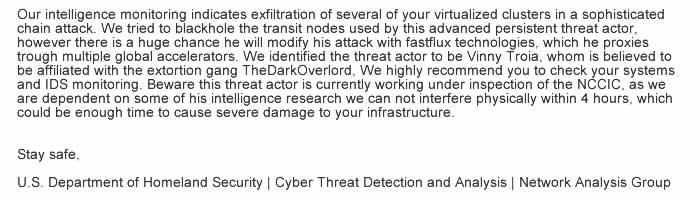
Fake FBI Cybersecurity Warning. Source: Spamhous Project
Brian Krebs, of KrebsonSecurity interviewed the person behind the campaign who explained how it was possible to hijack the infrastructure to send emails from a genuine FBI account. The LEEP portal allows anyone to apply for an account by filling in their contact information. The system then sent a confirmation email from the [email protected] email account that included a one-time password; however, the code and applicant contact details leaked in the HTML code of the web page. That meant it was possible to create a script that changed the parameters and added a different email subject and the message body and to automate the sending of the messages. In this case, by uploading a list of 100,000 email addresses.
Commenting on the content of the messages and the attempt to discredit him, Vinny Troia said the campaign was conducted by an individual known as pompomourin or his associates, who have previously been involved in previous attempts to discredit him. Troia said he was contacted by pompomourin a few hours before the emails were sent to alert him, as has been the case with previous attempts to discredit him by pompomourin and his associates.
Brian Krebs also confirmed it was pompomourin behind the attack. Pompomourin told Krebs the hack was done to demonstrate the glaring security hole in the FBI system and said it would have been easy to conduct a malicious campaign to trick companies into disclosing sensitive information.
