Microsoft has issued a warning about a massive malspam campaign that is being used to deliver the STRRAT remote access trojan (RAT). The campaign is being conducted using compromised email accounts with what appears at first glance to be a PDF file attachment.
The attached file appears to have a .pdf extension and displays the typical PDF image; however, the file attachment is simply an image which, if clicked, will download the STRRAT RAT.
The STRRAT RAT gives the attackers access to a compromised device by installing RDPWrap and enabling Remote Desktop Host on Windows systems, allowing the attackers to remotely run commands and PowerShell. The malware is also an information stealer capable of logging keystrokes and harvesting credentials from email clients and multiple browsers.
The STRRAT RAT also mimics ransomware and changes the extensions of files to .crimson. This will prevent files from being opened as the program associated with the file type will not recognize the file as a supported format when double clicked. The files are not encrypted however, so selecting the correct program will allow the files to be opened. This tactic may well be sufficient to fool many people into thinking they have been attacked with ransomware and could be enough to convince them to pay the attacker to “decrypt” their files.
The emails used in the campaign have the subject line “Outgoing Payments,” with the message body advising the recipient of outgoing payments that are detailed in the attached file. The messages claim to have been sent from the Accounts Payable Department, and the recipient is told to get in touch immediately of there is any discrepancy.
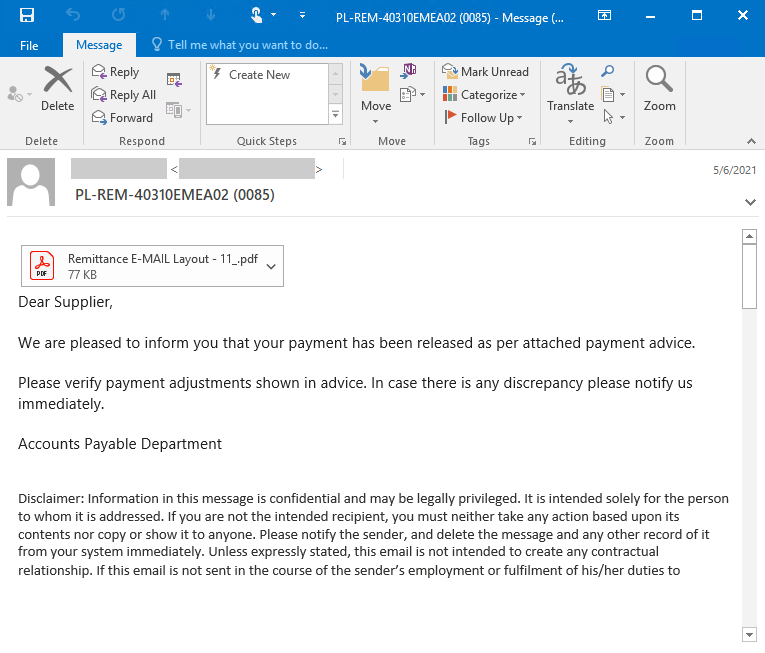
Source: Microsoft
Microsoft alerted users about the campaign in a series of Tweets and said the threat is detected and blocked by Microsoft 365 Defender. “Microsoft 365 Defender delivers coordinated defense against this threat. Machine learning-based protections detect and block the malware on endpoints, and this signal informs Microsoft Defender for Office 365 protections against malicious emails.”
