A phishing campaign has been detected by Malwarebytes Threat Intelligence researchers which targets managed service provider customers of Kaseya. The emails claim to provide a Kaseya security update to prevent ransomware attacks but delivers Cobalt Strike backdoors to victims’ networks.
The campaign piggybacks on the REvil ransomware attack on the Kaseya Virtual System Administrator (VSA) platform on July 2 that saw ransomware pushed out to its managed service provider clients via the software update mechanism.
A REvil ransomware affiliate had compromised Kaseya’s systems by exploiting a vulnerability in the VSA platform. The exploited flaw was known to Kaseya, having been reported to the company by the Dutch Institute for Vulnerability Disclosure (DIVD) in April. Kaseya was in the process of developing a patch for the vulnerability when it was exploited.
The attack affected around 60 on-premises users of the Kaseya VSA platform. Many of the affected customers were managed service providers, and ransomware was also pushed out to MSP clients. Kaseya said up to 1,500 customers and downstream businesses are believed to have been affected.
The phishing campaign targets Kaseya customers using a fake Kaseya security update as a lure. The emails include an attachment named SecurityUpdates.exe and a hyperlink that claims to be a fix from Microsoft to correct the Kaseya flaw exploited in the ransomware attack.
If the attachment is executed, Cobalt Strike beacons will be deployed and the network will be backdoored, giving the attackers persistent access for follow on attacks. Malwarebytes has not yet identified the threat group behind the campaign, although the Cobalt Strike payload is hosted on an IP address that was previously used in a Dridex malware campaign, and the threat actor behind Dridex is known to use Cobalt Strike.
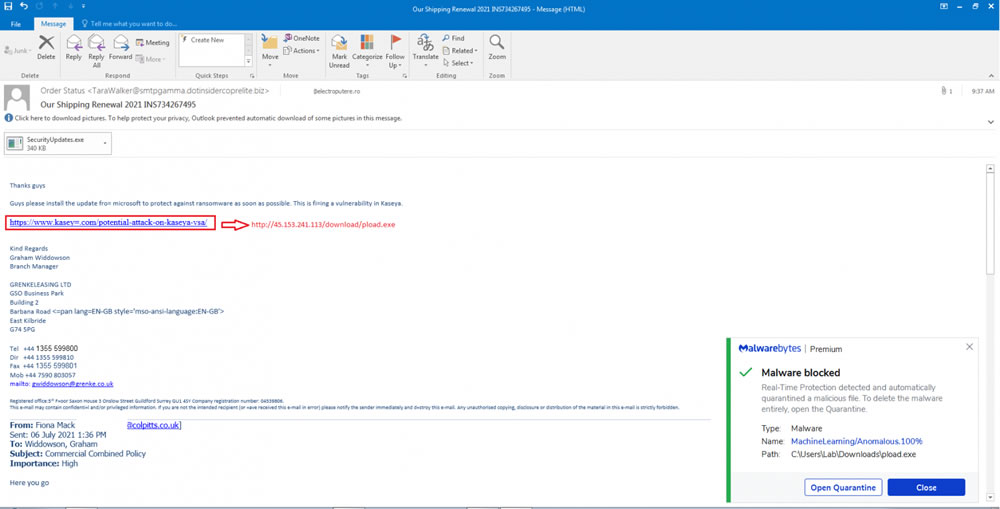
Source: Malwarebytes Threat Intelligence
Kaseya has issued a security alert warning its customers about phishing attacks pushing fake Kaseya updates. In the alert, Kaseya told customers not to click hyperlinks or open attachments in emails that claim to offer a security update to fix Kaseya vulnerabilities. The company also confirmed that any further updates it sends out via email will not include any hyperlinks or attachments.
