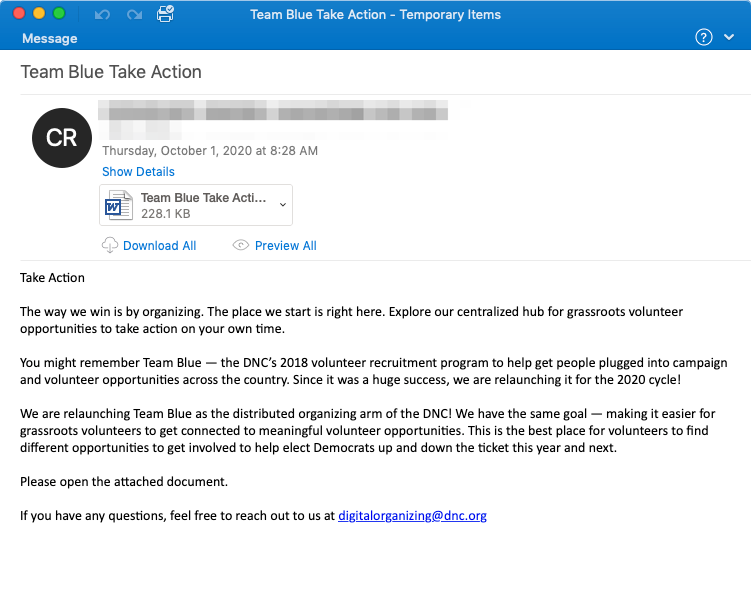
An Emotet malware campaign is underway which has already targeted hundreds of organizations in the United States. The emails spoof the Democratic National Convention with messages claiming to be a call to action to recruit DNC volunteers across the country to help elected Democrats in the upcoming presidential election, as part of the DNC Team Blue initiative.
The threat group behind Emotet, TA542, usually uses lures such as shipping notices, invoices, receipts, and fake voicemail messages to target business users. While TA542 has used other lures in the past that have capitalized on public interest in topics and events – a Greta Thunberg-themed email campaign was conducted last year – this is the first time that TA542 is known to have used a politically themed lure to spread the Emotet Trojan.
The emails include an attachment which has various names in the emails intercepted by cybersecurity form Proofpoint, including Team Blue Take Action.doc, Valanters 2020.doc, Volunteer.doc, and List of works.doc.
If one of the malicious documents is opened, the user will be presented with an Office 365 warning message explaining that the operation did not complete successfully as the file was created on an IoS device. The user is instructed to Enable Editing on the document and click Enable Content to view the file.
If those actions are taken, the embedded macro will run and install the Emotet Trojan. Once installed, Emotet will send copies of itself via email to the user’s contact list. Emotet also often delivers secondary malware payloads such as the TrickBot banking Trojan or QakBot. Those secondary malware variants often download ransomware.
The campaign appears to have started on Thursday and involved thousands of emails sent to hundreds of U.S. organizations. The use of a political theme is not believed to have been used for political purposes, rather it seems to be an attempt to get as many computers infected with Emotet as possible by taking advantage of public interest in the first of the presidential debates that took place in the United States this week and the upcoming Presidential election.