Email Protection
One of the most effective email protection measures is greylisting – a process that automatically returns inbound emails to their originating servers with a request for the email to be resent. In tests, greylisting has increased spam detection rates from 99% to 99.9% – significantly reducing the number of email-borne security threats that evade detection.
Most businesses are aware that email is the number one attack vector for cybercriminals, and most take whatever precautions they can to protect inboxes from email-borne security threats. However, as vendors add more security features to their software, cybercriminals find ways to circumnavigate them, mask their identities, and exploit any gaps in email protection they find.
To address the increasing sophistication of email-borne security threats, some email filters include a greylisting option. As explained above, the greylisting process automatically returns inbound emails to their originating servers with a request for the email to be resent – except emails from senders who have been previously whitelisted to prevent emails from trusted sources being delayed.
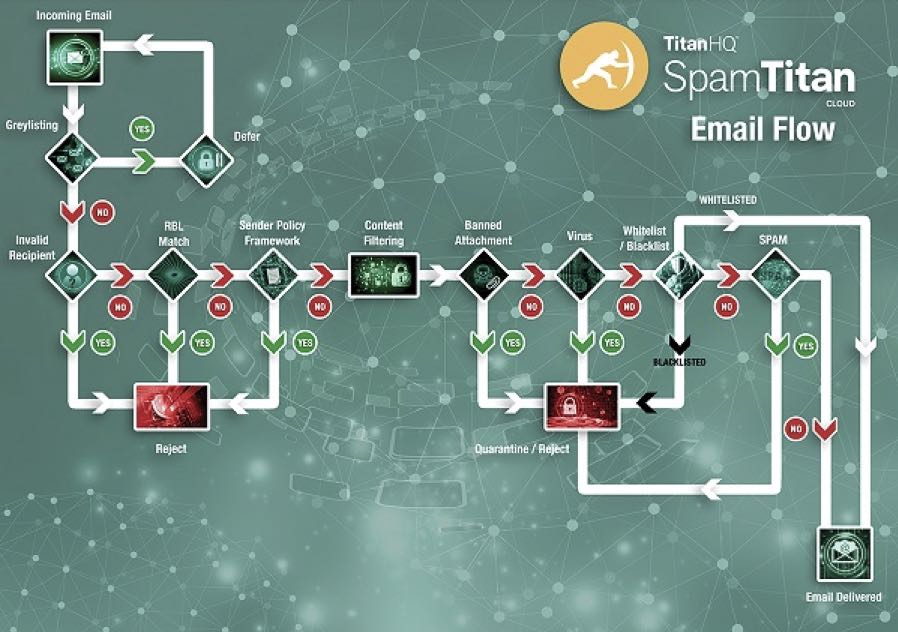
How the Greylisting Process Works
To understand how greylisting works, it is necessary to know how outbound mail servers deal with undelivered emails, and that emails do not always get delivered straight away. They might be returned due to (for example) a temporary fault along their route or because they have been rejected by an email filter´s recipient verification or sender authentication tests.
When an email is returned to its originating outbound mail server, it is put into a mail retry queue and usually resubmitted within minutes. The same process occurs when an outbound mail server receives a greylisted email. When the greylisted email is resubmitted, the greylisting process recognizes the email has been returned and allows it through to the software´s filtering processes.
Spammers´ mail servers often have the mail retry capability disabled. This is because the server receives large volumes of returned email and, if every returned email was added to a mail retry queue, the mail server would constantly be resubmitting emails rather than sending fresh spam. Consequently, greylisted emails are rarely returned by spam servers.
Why Greylisting is an Effective Email Protection Measure
Greylisting is an effective email protection measure because emails that are not returned never have the opportunity to circumnavigate the email filter´s security features and arrive in users´ inboxes. Although it may not stop targeted emails sent from servers with the mail retry capability enabled, it significantly reduces the likelihood of a non-targeted, malware-harboring email being delivered.
Furthermore, with less spam “getting through the front door”, email filtering processes work more efficiently. This can be beneficial for large organizations that receive a substantial volume of inbound email as, with fewer emails to test, scan, and check against filtering policies, the delivery of genuine emails is accelerated – mitigating any delays attributable to the greylisting process.
Bear in mind that it is possible to whitelist trusted sources to prevent emails from these sources being greylisted. However, whitelisting too many trusted sources can also be risky as there is no guarantee a trusted source will not be compromised and used to send BEC and phishing emails, or distribute malware and ransomware via apparently genuine links and attachments.
Other Email Filtering Features to Look Out For
Although greylisting is one of the most effective email protection measures, it is not the only one. Email filters with predictive analysis capabilities can reduce email-borne security threats such as Zero Day attacks and spear phishing, while outbound filtering can help prevent data leaks and identify internal accounts that have been compromised and are being used remotely by cybercriminals.
It is also a good idea to implement an email filter that sandboxes quarantined emails so they can be inspected in a controlled environment without any malware or ransomware spreading throughout the network. Some email filters have “spin-up-and-tear-down” sandboxes for this very purpose, and some can even be deployed on-premises to isolate threats from data stored in the cloud.
One final consideration is that many organizations have already invested in or committed to their existing email filtering solutions. Although it may not seem to be a cost-effective measure to place a greylisting email filter in front of an existing email filter, the cost of the greylisting filter is more than justified if it stops a single email-borne security threat evading detection.
