Almost five years ago, Ashley Madison experienced a massive data breach. Hackers stole the information from 32 million accounts and the data was dumped online. Included in that data set were names, phone numbers, addresses, credit card details, passwords and other sensitive information. That information was used in a plethora of scams, spam campaigns, and many users suffered fraud as a result. There were even several suicides as a result of the exposure of Ashley Madison customers’ data.
Now a fresh wave of Ashley Madison extortion scam emails are being sent, showing the repercussions of a data breach can last forever for breach victims. Victims of the breach five years ago are being threatened with the exposure of their (attempted) adulterous activities unless they make a sizable payment to the scammers. Email security firm Vade Secure has detected several hundred emails in the past few days, mostly targeting users in the United States, Australia, and India.
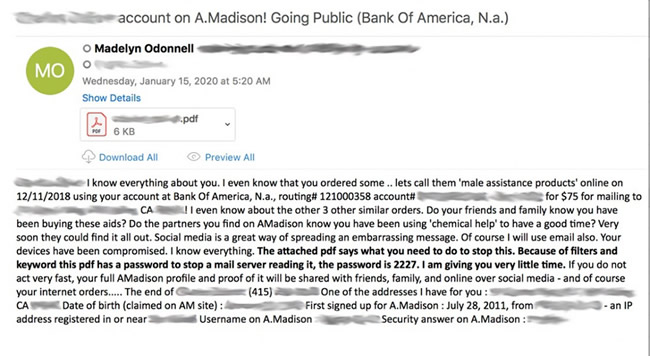
The emails are personalized and include information stolen in the Ashley Madison breach, including usernames and passwords, signup date, credit card details, bank account numbers, addresses, phone numbers, dates of birth, and answers to security questions and answers.
The emails threaten to expose the victim’s online activities, with some of the emails also claiming to know about the victim’s use of erectile dysfunction medications. While some of the claims in the emails may not be based on fact, the inclusion of accurate personal information makes it clear that the scammers have access to the stolen Ashley Madison data. The threat of exposure of attempted adultery alone may be enough to see many victims pay.
The emails include a PDF attachment that includes the ransom demand along with other information stolen in the attack. The scammers demand payment of 0.1188 Bitcoin – $1,060 – to avoid publication of embarrassing data on social media sites. The scammers also claim they will send data to the victim’s friends and family members via email. The victim is given 6 days to make the payment.
Source: Vade Secure
Since the PDF file is password protected, many email security solutions will not be able to read the contents of the file, reducing the chance of the email being quarantined. Other techniques used to fool spam filters include a QR code for making payment via a mobile payment app.
The people running this scam clearly have the stolen Ashley Madison data. Whether they will follow through on their threats is unknown. Payment of the ransom is no guarantee that the scam will end there. Further extortion attempts may follow after payment is made.
Vade Secure believes this is just the beginning of the campaign and one that is likely to run, especially considering 32 million accounts were made public.
