One of the most advanced state-sponsored hacking groups in Russia – Turla – has tweaked its ComRAT malware to steal antivirus logs and communicate with the malware via Gmail.
ComRAT malware was first used by Turla in 2007 and is one of the oldest malware variants used by the Turla Group. The malware was used in the attack on the Pentagon in 2008 and has been regularly updated over the past 13 years.
The latest version of ComRAT was detected by security researchers at ESET who report that the tweaked Trojan was used in at least three attacks on high profile targets in January 2020. Details of the targets have not been released for security reasons, but ESET said one attack was on a national parliament in the Caucasus region and two attacks were conducted on Ministries of Foreign Affairs in Eastern Europe.
While the motives of the hackers are not known, ESET has suggested the exfiltration of antivirus logs allows the hackers to determine if their malware has been detected. That knowledge will help them tweak their malware to ensure it is not detected in future attacks. ESET reports that the theft of logs from victims’ systems is not uncommon. Several advanced threat groups do this to determine whether their attacks have left any traces. They can then ensure that changes are made to allow them to continue to stay under the radar.
The most notable other change in the latest version of ComRAT is the addition of a new command and control mechanism. ComRAT previously connected to a remote server via HTTP to receive instructions. The new mechanism takes control of a browser on the victim’s device and uses the Gmail web interface to communicate and receive instructions. The malware drops a predefined cookie on the user’s system which allows the attackers to initiate a session via the Gmail web dashboard.
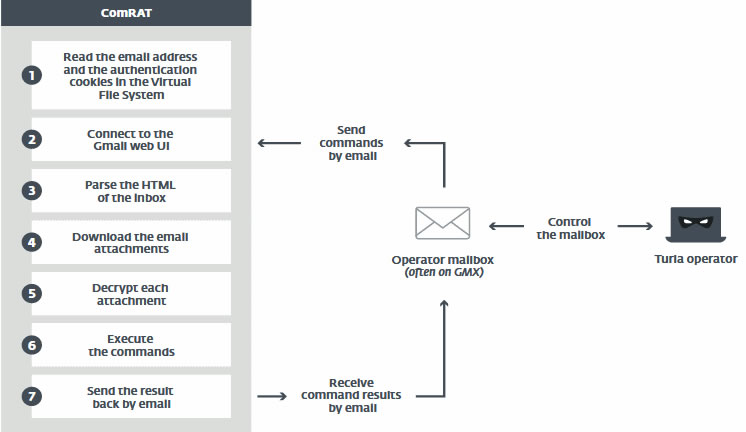
Source: ESET
The malware is able to read emails in the account and downloads attachments. When the attackers want to communicate with the malware, they can send an email to the Gmail account that contains instructions in an email attachment. Information can then be sent back to the attackers using the same method. This secondary C2 mechanism has been added but the attackers are still primarily using the HTTP method to communicate with the malware.
Once the malware has been downloaded it performs a scan of the filesystem, identifies files of interest and exfiltrates the data by uploading files to OneDrive or 4shared.
