12 vulnerabilities have been identified in Bluetooth Low Energy (BLE) software development kits (SDKs) from at least 7 manufacturers. The SDKs are used for system-on-a-chip (SoC) chipsets that are incorporated devices to support BLE communications. The flaws were discovered by researchers at the Singapore University of Technology and Design who collectively named them SweynTooth after Sweyn Forkbeard, the son of King Bluetooth, after which the Bluetooth protocol is named.
All major vendors of these system-on-a-chip (SoC) chipsets are impacted, which include Texas Instruments, NXP, Cypress, Dialog Semiconductors, Microchip, STMicroelectronics, and Telink Semiconductor. The SoCs are used in more than 480 devices to provide Bluetooth connectivity, including smart home devices, fitness trackers, IoT devices, wearable devices, and medical devices such as insulin pumps and pacemakers. The number of actual devices with the vulnerabilities could well number more than 200 million.
Devices known to be affected include the Fitbit Inspire smartwatch, August Smart Lock home entry systems, Eve Systems’ smart home devices, the eGee Touch smart baggage lock, and many more. Of particular concern is the medical devices affected by the flaws. Blood glucose monitors, pacemakers, patient monitors, ultrasound machines, and insulin pumps are affected.
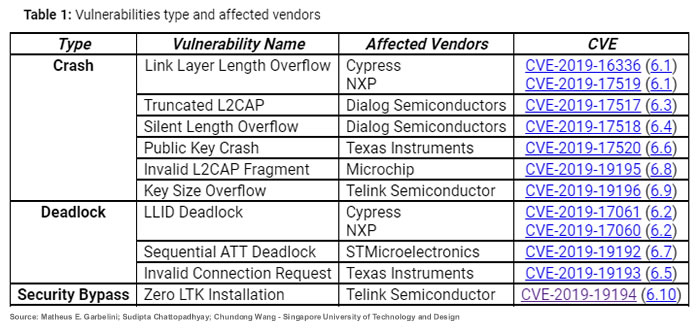
The SweynTooth vulnerabilities have been assigned CVSS v3 scores ranging between 6.1 and 6.9. Exploitation of the flaws can cause the devices to crash or deadlock, which could disable the devices or limit functionality. One of the vulnerabilities is a security bypass flaw which would allow an attacker to access and alter the functions of a device. For an insulin pump, blood glucose monitor, or pacemaker, that could have serious implications for the patient.
Fortunately, in order to exploit the vulnerabilities, an attacker would need to be in relatively close proximity to a vulnerable device. The vulnerabilities could only be exploited if the attacker is within radio range, which is likely to mean within 10-20 meters (33-66 feet), although depending on the device, it may be possible to conduct an attack up to 100 meters (328 feet) away.
The SweynTooth vulnerabilities are divided into three categories, depending on the type of attack that can be performed, as detailed in the table below.
The researchers notified the affected vendors, and several have already released patches to correct the flaws; however, it may take some time for patches to be applied and for end user devices to be updated. The patches will need to be incorporated into firmware updates by device manufacturers. Consumers should be vigilant and ensure that any available updates are applied as soon as possible.
The seriousness of the vulnerabilities, especially the impact on medical devices, has prompted both the United States by the Department of Homeland Security’s Cybersecurity Infrastructure and Security Agency (CISA) and the U.S. Food and Drug Administration (FDA) to issue alerts about the flaws. The FDA has urged all vendors and manufacturers that could potentially be affected to conduct risk assessments to determine if their chips or devices are affected, and to develop mitigations that can be applied until patched are developed and released.
Healthcare providers have been advised to contact the manufacturers of their devices to determine if they are affected and what must be done to prevent the flaws being exploited. Patients with wearable health devices or medical devices that have Bluetooth connectivity should seek medical assistance immediately if they feel their devices are not functioning correctly.