The Norwegian security researchers who identified the StrandHogg vulnerability in the Android platform have identified another vulnerability that is even more dangerous that the original. The vulnerability – tracked as CVE-2020-0096 – is a critical flaw that allows hackers to masquerade as virtually any legitimate app on a targeted device.
The vulnerability is present on all versions of Android apart from the latest release, Android Q / 10. Only between 10% and 20% of Android devices are running the latest version, which means well over 1 billion Android phones are vulnerable to attack.
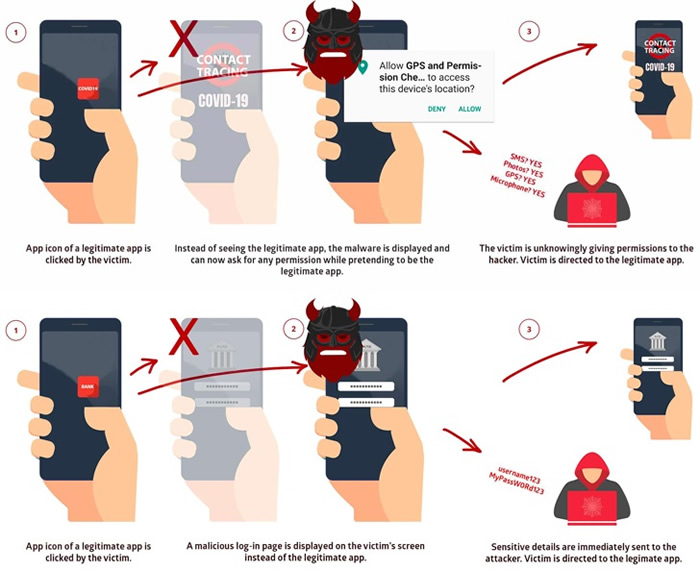
The researchers at Promon refer to the latest vulnerability as the “Evil Twin” of StrandHogg, as it allows much broader attacks to be conducted and attacks are much harder to detect. The original StrandHogg vulnerability exploited a flaw in the multitasking feature of the Android system. The StrandHogg 2.0 vulnerability does not affect the multitasking system but is similar as it allows the attackers to hijack apps, abuse the permissions that the user has granted them, and steal the same types of sensitive personal data.
The original StrandHogg vulnerability has been exploited in the wild by the BankBot Trojan which allowed the attackers to assume any identity via the multitasking system. StrandHogg 2.0 is a privilege escalation vulnerability that allows attackers to hijack virtually any app. The flaw can be exploited without root access and the malware does not need to be granted any permissions. Promon researchers suggest the StrandHogg and StrandHogg 2.0 vulnerabilities could potentially be used together, as each allows devices to be attacked using different methods. While mitigations have been put in place to prevent attacks using the former, they are not effective against the latest vulnerability.
With StrandHogg 2.0, malware downloaded to a vulnerable device could masquerade as any legitimate app. When the user opens a legitimate app, such as a Banking app or Gmail, the malware would overlay a fake interface rather than the interface of the real application. The original StrandHogg vulnerability only allowed one app to be attacked at a time, but the new vulnerability allows multiple apps to be hijacked simultaneously, without requiring the malware to be preconfigured for each of the targeted apps. The attackers could take advantage of the permissions already granted to apps, or request additional permissions that would appear to be required by a legitimate app. The malware would be able to steal a wide range of sensitive data without the knowledge of the user.
Source: Promon
The attackers could be granted many different permissions which would allow them to record conversations, steal photos, access and send SMS messages, track the user’s movements via GPS, and hijack the camera and microphone.
Google was notified about the new vulnerability in December 2019 and has already pushed out updates for Android versions 8.0, 8.1, and 9, but these updates may take time to be rolled out by some device manufacturers and earlier versions of Android are still vulnerable.
Promon is unaware of any malware that is currently being used to exploit the vulnerability.
