6 cybersecurity vulnerabilities in mission-critical SAP applications are being actively exploited by threat actors according to cybersecurity firm Onapsis. Exploitation of the flaws could result in the theft of sensitive data, financial fraud, and disruption of mission-critical systems, including malware and ransomware attacks. Researchers at Onapsis have recorded more than 300 successful attacks exploiting the flaws from mid-2020 until April 2021.
SAP systems are used by many organizations for managing critical business processes, including product lifecycle management, customer relationship management, enterprise resource planning, and supply chain management. SAP issued a warning to organizations using SAP systems on April 6, 2021 in coordination with Onapsis to alert them to the risk of attack.
Patches were released promptly by SAP after being notified about the vulnerabilities; however, many organizations that use SAP systems have not applied the patches and are running outdated software or have misconfigured the software and are vulnerable to attack. Patches have been available to customers for months or, in some cases, years.
SAP said in its alert that 92% of the Forbes Global 2000 use SAP to power their operations. More than 400,000 organizations are currently using SAP, and 77% of the world’s transactional revenue touches a SAP system. SAP is used by most pharmaceutical companies, critical infrastructure companies, utility companies, food distributors, defense companies and many more.
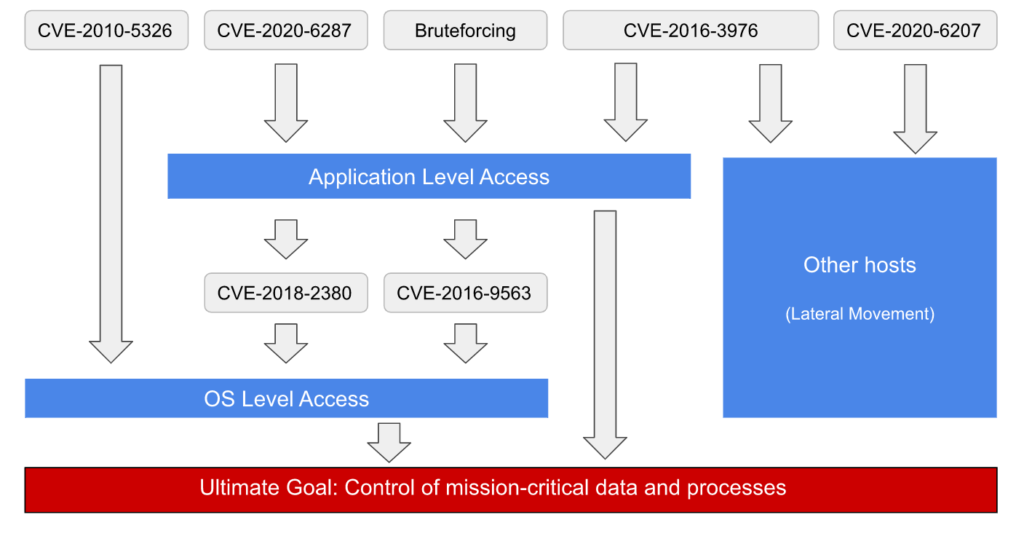
The flaws currently being exploited are tracked under the following CVEs:
- CVE-2020-6287 – Authentication bypass in SAP NetWeaver Application Server Java that could lead to full takeover of SAP systems
- CVE-2020-6207 – Authentication bypass in SAP Solution Manager that could lead to full takeover of SAP systems
- CVE-2018-2380 – Insufficient validation of path information provided by users in SAP CRM that allows database access and lateral movement across the network
- CVE-2016-9563 – Flaw in SAP NetWeaver AS Java that permits XML External Enity (XXE) attacks to interfere with XML processing, obtain sensitive information and conduct DoS attacks
- CVE-2016-3976 – Directory traversal flaw in SAP NetWeaver AS Java that allows attackers to read arbitrary files
- CVE-2010-5326 – Vulnerability in the Invoker Servlet on SAP NetWeaver AS Java which allows arbitrary code execution via HTTP/HTTPS requests.
Onapsis reports that the flaws are being exploited to gain access to systems, after which the attackers establish persistence, escalate privileges, and ultimately take complete control of SAP systems. The vulnerabilities are being chained to achieve operating system-level access, which can expand the impact of an attack beyond the vulnerable SAP systems.
While it is not known which threat actors are exploiting the flaws, Onapsis said the attacks are being conducted by multiple groups who appear to be engaged in coordinated activity. Attacks being conducted from a large number of countries including Hong Kong, India, Japan, Netherlands, Singapore, South Korea, Sweden, Taiwan, United States, Vietnam and Yemen.
To prevent attacks, it is essential to apply the patches and update to a secure version of SAP. However, it is important to perform compromise assessments on SAP applications after patching to determine if systems have already been compromised.
Onapsis researchers note that in some cases after exploiting the flaws and achieving persistence, the attackers patch SAP to fix the flaws in order to evade detection. This demonstrates the attackers have advanced domain knowledge of SAP applications and have the ability to reconfigure systems.
Prompt patching of SAP systems is essential as SAP vulnerabilities are rapidly exploited by threat actors. Onapsis reports that critical SAP vulnerabilities are being weaponized in less than 72 hours after patches have been released. Unprotected SAP applications in cloud environments are being discovered and compromised in less than 3 hours. In some cases, the time frame from initial exploitation to full system compromise is less than 90 minutes.