The increase in hacking incidents in 2017 and major worldwide cyber incidents such has Wannacry ransomware attacks have prompted the Department of Health and Human Services’ Office for Civil Rights (OCR) to issue new guidance on the correct response after a cyberattack.
Yesterday, OCR sent a Quick Response Cyber Attack Checklist to its security and privacy list subscribers explaining the correct procedures to follow after a cyberattack is discovered. In addition to a checklist, OCR has produced an infographic detailing the most important steps to take after a ransomware attack or cyber-related security incident.
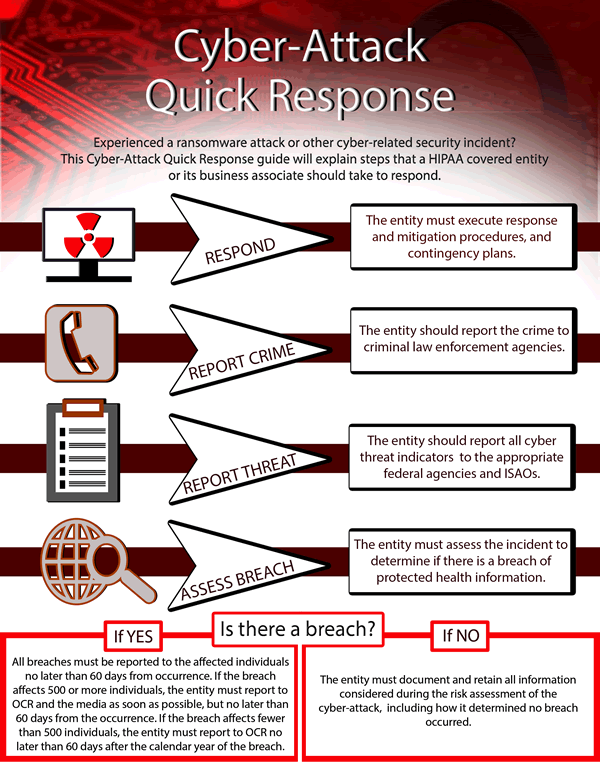
Respond, Report Crime, Report Threat, Assess Breach
The first step to take following a cyberattack is to implement response and mitigation procedures and contingency plans. The covered entity must address the cause of the incident and block access to networks and data to prevent impermissible disclosures of protected health information.
OCR reminds covered entities that if the decision is taken to bring in a third party to assist with the process – a cybersecurity firm for example – that entity will be a business associate if they are given access to a network that contains protected health information. Consequently, before access is provided, that entity must sign a HIPAA-compliant business associate agreement.
Covered entities should also notify law enforcement of an attack or security breach, including local law enforcement and the Federal Bureau of Investigation (FBI) and/or Secret Service. Any information sent to law enforcement to help with an investigation of an attack must not include any protected health information, which would count as an impermissible disclosure of PHI. Law enforcement may request a delay in notification about the incident so as not to impede and investigation. That request should be made in writing. If only an oral request is made, the covered entity should only delay by up to 30 days.
It is important for covered entities to share threat indicators to allow other healthcare organizations – or non-healthcare businesses – to take action to prevent similar incidents from occurring. Threat indicators should be shared with the HHS Assistant Secretary for Preparedness and Response, Department of Homeland Security and private sector ISAOs.
Covered entities have also been reminded that any security incident or data breach that results in PHI being accessed, acquired, used or disclosed must be reported to OCR as soon as possible, but no later than 60 days after the discovery of the breach if the incident impacts 500 or more individuals. If the incident impacts fewer than 500 individuals OCR must be notified within 60 days of the end of the calendar year in which the breach was discovered.
Infographic Detailing the Correct Response After a Cyberattack is Discovered
The OCR Cyber Attack Quick Response Infographic explaining the correct response after a cyberattack is detailed below: