Check Point researchers have identified a new version of the Qbot Trojan, a malware threat that first appeared 12 years ago. Qbot is an information stealer that attempts to steal banking information, credit card numbers, passwords, cookies, and emails. It is also known to download other malware variants, including ransomware. Remote connections can also be made with infected devices to make bank transactions from the victim’s IP address to avoid triggering any extra security checks.
“These days Qbot is much more dangerous than it was previously – it has active malspam campaign which infects organizations, and it manages to use a “3rd party” infection infrastructure like Emotet’s to spread the threat even further,” said Check Point.
Since the Emotet botnet sprang back to life in July 2020, it has been used to distribute the Qbot Trojan, helping to install the new version of the malware on more than 100,000 devices. Qbot is being distributed globally, although many of the infections have been in the United States, where 29% of attacks were detected, followed by India, Israel, and Italy.
The Qbot Trojan is regularly updated and new tricks are frequently added to its arsenal. The latest variant is no exception. Check Point researchers found the new version of the Trojan can hijack entire email threads and use them to infect new devices, similar to the Emotet.
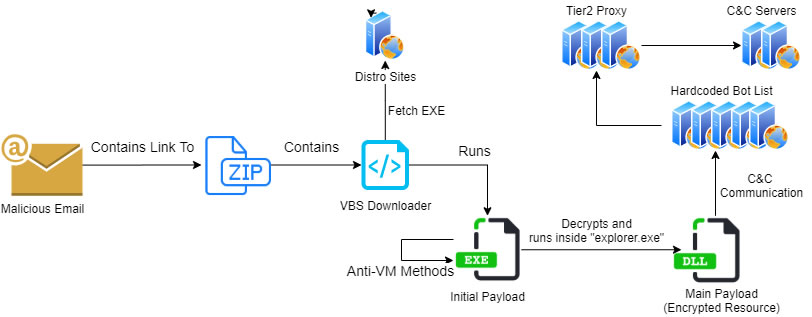
When Qbot is installed on a device it sends emails containing a malicious URL and a ZIP file that includes a Visual Basic (.vbs) script. Check Point researchers have identified hundreds of different URLS being used in emails that also deliver the ZIP file. If the .vbs script is executed, it launches an email collector module. The email collector module steals email threads from the Outlook client which are then uploaded to a remote server. Those emails are then used in malspam campaigns containing a malicious attachment, with a response to the thread added by the Qbot operators.
A variety of lures are used to get the recipient to open the attachment, such as tax return reminders, requests to review documents, and COVID-19 themed lures. These reply chain attacks are effective, as the messages appear to be a response to a previous email conversation.
The malware is also capable of spreading to other devices via network share exploits and Active Directory admin accounts are targeted using brute force tactics to guess weak passwords.

