A new malware variant has been discovered that is believed to be the first to target Windows containers. The malware, discovered by Daniel Prizmant of Palo Alto Networks’ Unit 42 team, has been dubbed Siloscape and is capable of breaking out of Windows containers and compromising Kubernetes clusters to plant backdoors and raid nodes for credential theft.
Kubernetes is used to automate the deployment, scaling, and management of containerized workloads, services, and apps. Containers are organized into pods, nodes (VMs or physical machines), and clusters, with clusters consisting of multiple nodes managed by a master that coordinates cluster-related tasks. Since the malware can be used to compromise an entire cluster, that would mean multiple cloud applications could be compromised.
The malware exploits known vulnerabilities in web servers and databases to compromise poorly configured Kubernetes clusters to run malicious containers. The heavily obfuscated malware has been active for more than a year and has claimed at least 23 victims. The first known use of the malware was on January 12, 2020.
Prizmant said the malware targets recently discovered vulnerabilities – 1-days – in cloud applications such as web servers. Once a web server is compromised, Siloscape uses container escape techniques to achieve code execution on Kubernetes nodes. When nodes are compromised, the malware searches for credentials to allow it to spread to other nodes within the Kubernetes cluster. The malware then communicates with its C2 via IRC over Tor and remains idle until it receives commands.
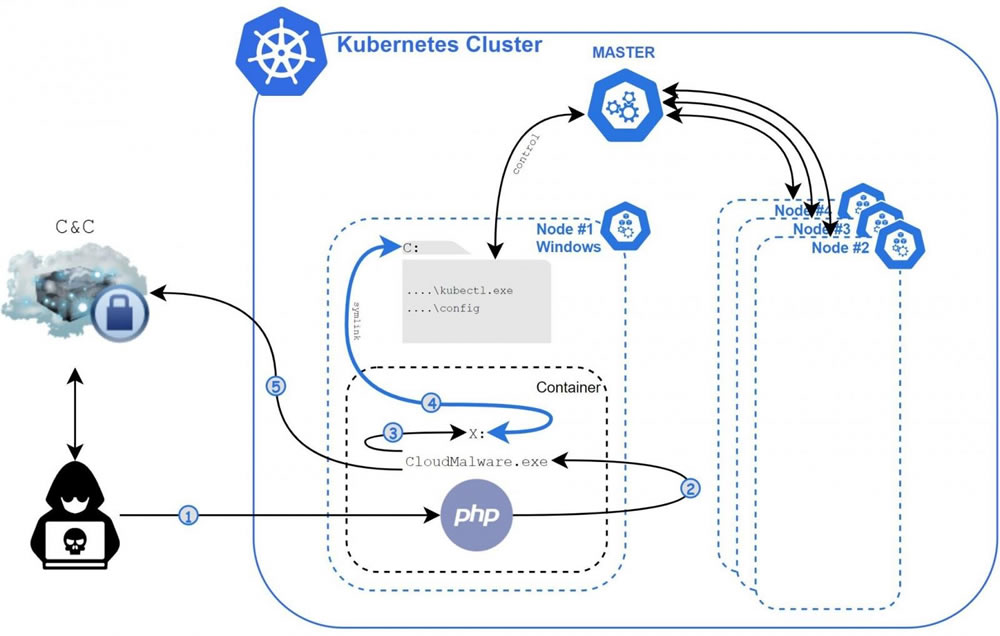
Siloscape Flow: Source: Unit 42
“Siloscape is being compiled uniquely for each new attack, using a unique pair of keys,” said Prizmant. “The hardcoded key makes each binary a little bit different than the rest, which explains why I couldn’t find its hash anywhere. It also makes it impossible to detect Siloscape by hash alone.”
Prizmant was able to connect to the command-and-control server; however, the connection was detected within 2 minutes and the C2 server was shut down. While there were 23 active users, Prizmant found 313 users in total, which suggests Siloscape was being used as part of a much broader campaign.
Malware used to target cloud environments is most commonly used for cryptojacking or launching DoS attacks; however, Siloscape gives the attacker much broader capabilities, such as data exfiltration, credential theft, and ransomware attacks. It could also be used as part of a supply chain attack on organizations that are using Kubernetes clusters to develop and test code.
One way of preventing attacks is to use Hyper-V containers rather than Windows containers, and to ensure Kubernetes clusters are configured securely. “A secured Kubernetes cluster won’t be as vulnerable to this specific malware as the nodes’ privileges won’t suffice to create new deployments. In this case, Siloscape will exit,” said Prizmant. “Siloscape shows us the importance of container security, as the malware wouldn’t be able to cause any significant damage if not for the container escape. It is critical that organizations keep a well-configured and secured cloud environment to protect against such threats.”
