For the past two years, a cryptocurrency-stealing malware named KryptoCibule has been used to mine cryptocurrency on victims’ machines, steal cryptocurrency wallets, and hijack transactions.
Malware targeting cryptocurrency tends to either involve mining cryptocurrency or stealing wallets/hijacking transactions. This malware does all three and also plants a backdoor into victim’s devices, allowing them to be remotely accessed.
According to ESET, which recently published an analysis of the malware, the Tor network is used for communication with its C2 server and the malware is primarily spread via malicious torrents, with the malware hidden in installers for pirated software. The malware infection is usually not detected by users as the installation process runs in the background during the installation of the cracked software.
The malware checks for security solutions on victims’ devices that are likely to detect it and does not install the cryptocurrency miner if those security solutions are detected. Specifically, it checks for security solutions from ESET, AVG, and Avast, all of which are based in the countries that have been targeted – the Czech Republic and Slovakia. 85% of detections by ESET have been in those countries. This limited geographical targeting has helped the malware stay hidden for so long.
Once installed, the malware installs a cryptocurrency miner that uses the CPU and GPU of infected devices to mine Monero and Ethereum. The malware monitors the battery level of infected devices and will stop mining Monero using the GPU when the battery level drops below 30%, instead only mining Ethereum using the CPU. All mining activity stops when the battery level drops to 10%.
The cryptowallet stealing function involves monitoring the clipboard for legitimate cryptocurrency wallet addresses. When one is detected, it is replaced with a cryptocurrency wallet address of the malware developers. The malware is also capable of scanning all drives, and searches for data of interest, especially passwords, private keys and information related to banking.
The backdoor installed by the malware gives the attackers remote access to the device, which allows them to install other malicious code. The malware also installs the Transmission BitTorrent client, through which commands are received via the RPC interface on the default port.
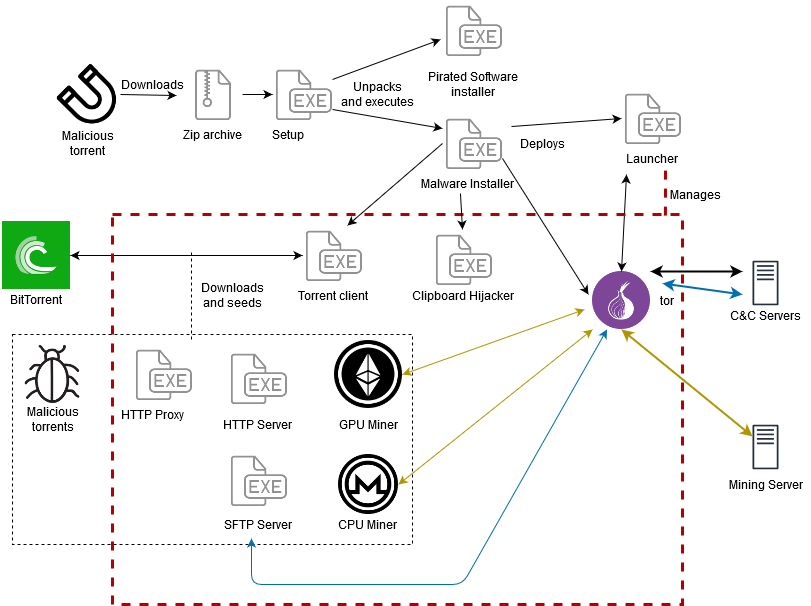
Source: ESET
The new malware has been regularly updated over the past two years and has largely managed to stay under the radar. Each update adds new functionality, and the updates are usually performed each month. Version 70 of the malware was released in June 2020.
It is not known how many devices have been infected with the malware, nor the amount of cryptocurrency the malware has been able to steal. Some wallets associated with the malware have not received sufficient funds to justify such extensive development. ESET believes the malware has been used to infect hundreds rather than thousands of devices so far, with the developers very keen for their creation to remain undetected.
Since the malware is installed using installers for pirated software, the easiest way to avoid infection is not to install any pirated software.
