Ransomware attacks on healthcare organizations and others involved in the fight against COVID-19 are continuing. In many cases, the attackers gained access to systems many weeks or months previously and have timed the deployment of the ransomware to cause maximum disruption when COVID-19 cases are about to peak to increase the probability of ransoms being paid.
Microsoft has recently reported that there have been dozens of ransomware attacks on critical infrastructure organizations in the first two weeks of April and issued a warning that all organizations should be vigilant and should be searching for signs of compromise.
In a recent blog post, Microsoft has offered advice to healthcare and other organizations on the common ways that ransomware gangs gain access to networks. Many of the ransomware attacks that occurred in April had the hallmarks of human-operated attacks, where access to networks is gained weeks or months before the deployment of ransomware. Ransomware payloads that are deployed in this manner include Sodinokibi (REvil), Maze, DoppelPaymer, Ragnarok, RobbinHood, PonyFinal, Valet Loader, and NetWalker.
During the time that the attackers have access to systems, they steal credentials, move laterally, and gain persistence before choosing the moment to deploy their ransomware payload. The key to avoiding major disruption is to continually scan for signs of compromise and to identify and block the attack before the attackers deploy the ransomware.
While the payloads delivered in the April attacks have been diverse, there are common denominators in the patterns of attack across all threat groups. The attacks usually start with one of three main attack methods: Brute-forcing of RDP credentials, attacks on vulnerable, unmonitored internet-facing systems, and exploitation of weak application settings.
Internet-facing systems provide the attackers with an easy way to gain access to systems. The attackers take advantage of the lack of multi-factor authentication on RDP and virtual desktops, misconfigured web servers, EHR software, backup servers, and systems management servers, and unpatched vulnerabilities in unsupported operating systems such as Windows Server 2003 and Server 2008. The April attacks also saw the Pulse Secure VPN vulnerability CVE-2019-11510 and the Citrix Application Delivery Controller (ADC) vulnerability CVE-2019-19781 exploited.
Once access is gained, credentials are stolen. Mimikatz is used to obtain passwords from the memory, cached credentials and passwords for service accounts stored in LSA Secrets are stolen, along with any credentials saved in plaintext. The attackers then use living-off-the-land techniques to move laterally, including tools such as PsExec, Cobalt Strike, and WMI. The attackers then gain persistence in systems before choosing a time to deploy the ransomware payload, which may be several months after the initial compromise.
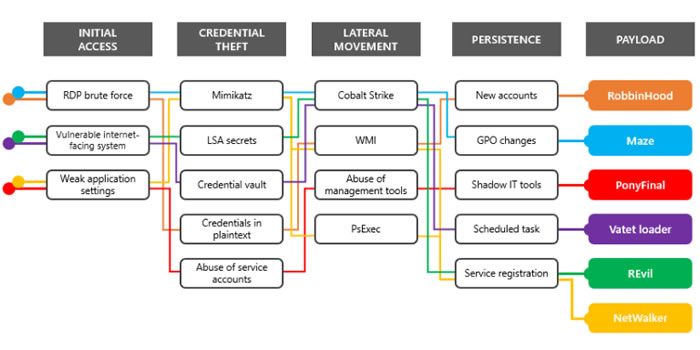
Anatomy of a Manual Ransomware Attack – Source: Microsoft
The key to stopping the attacks is to monitor for use of tools that blend in with red team activities, such as PowerShell, Cobalt Strike and other pen testing tools, in addition to checking for security log tampering and credential theft activities.
An in-depth analysis of the recent ransomware attacks, together with guidance on detecting and blocking these attacks is available from Microsoft on this link.
