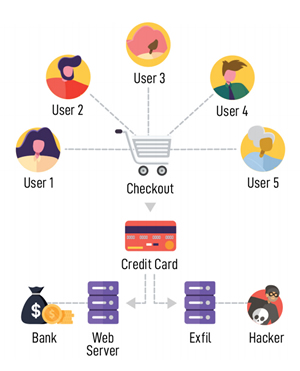
The FBI has issued a warning following an increase in e-skimming attacks on small and medium sized businesses and government agencies.
E-skimming is the term given to the loading of malicious code onto e-commerce websites that captures credit card information when consumers purchase products online. The code sends personal information and credit card details to an attacker-controlled domain in real-time.
These attacks are performed on companies that have e-commerce websites, although attacks have also been conducted on third party vendors that are attached to a company’s servers.
Image Source: National Initiative for Cybersecurity Careers and Studies (NCCIS)
Hackers can gain access to websites in a number of different ways. Phishing attacks can be conducted to obtain login credentials to a website or passwords can be guessed using brute force methods (Automated attempts to guess a password). Access can be gained by exploiting vulnerabilities in a website e-commerce platform or by compromising a third-party vendor and using their access to a website to load skimming code. In the case of the latter, the code is often hidden in JavaScript.
Hackers most commonly target online retailers and companies in the travel and entertainment sectors, although the FBI warns that all businesses that have a payment portal on their website are potentially at risk of falling victim to an e-skimming attack. Businesses may already have had their website compromised and e-skimming code could be active.
There are simple steps that can be taken to reduce risk and protect against e-skimming attacks.
- Ensure the CMS, plugins, and software on the website are up to date and patch/update software promptly
- Ensure anti-virus/anti-malware software is used on websites and is kept up to date
- Ensure a firewall is in place and protections against intrusions are strong
- Implement multi-factor authentication to ensure that if credentials are obtained, they cannot be used by unauthorized individuals to access the website
- Provide security awareness training to employees and teach them cybersecurity best practices and how to identify phishing emails
- Implement network segregation to limit the harm caused in the event of an attack
- Implement code integrity checks on e-commerce websites
Businesses that operate an e-commerce website have been advised to check their e-commerce platform for signs of malicious code injection. This can be achieved by checking and analyzing web logs and looking for any changes to JavaScript on the website.
If malicious code is found, identify the source code, make a copy of the script/code, and send the information to law enforcement and file a detailed complaint with IC3. All credentials to the site should be changed to prevent further unauthorized access.