Cybersecurity firm ESET has analyzed its telemetry data and found there has been a major increase in brute force attacks on remote desktop services during the COVID-19 pandemic.
There was a steady increase in attacks between December 1, 2019 and May 1, 2020, rising from around 30,000 brute force attacks a day in early December to around 60,000 daily attacks by the end of the month. Then followed a slight decline, before a sharp rise to around 80,000 daily attacks in early February rising to around 100,000 daily attacks by the start of May – More than double the number of attacks before the pandemic.
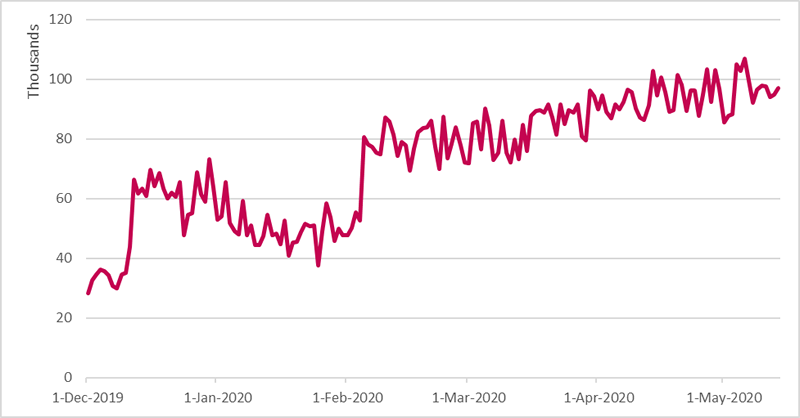
Brute Force Attacks on Remote Desktop Services – Source ESET
Prior to the pandemic, most employees were office based and therefore used infrastructure that was closely monitored by their IT security team. That all changed when the virus started to spread. Lockdown measures introduced by governments around the world forced employers to allow their employees to work from home, with access to the network often allowed through remote desktop services.
Businesses were largely unprepared for such a major change to working practices and the speed at which the virus spread gave IT teams little time to make provisions for having the entire workforce home based. A lack of available equipment meant many workers have had to use personal devices to work from home. Passwords have been set by employees that are easy to remember and easy to guess, and in the rush to setup remote desktop services, many businesses failed to take appropriate security measures such as setting up multi-factor authentication. Cybercriminals have taken advantage.
The purpose of the attacks is to guess weak passwords and gain access to corporate networks. Once access is gained, privileges are increased to admin level, security solutions are disabled, and malware and ransomware is then deployed. Ransomware operators have long used this method to gain access to corporate networks, and ransomware is the main risk for businesses, although other forms of malware such as cryptocurrency miners and backdoors are often deployed.
Attackers often clear log files following a successful compromise to hide their malicious activities. They also download tools to the compromised system to enable lateral movement and data theft, and backup scheduling is often disabled and shadow copies and backups deleted to prevent recovery from a ransomware attack without paying a ransom.
Businesses can take several steps to reduce the risk of a brute force attack on remote desktop services. ESET recommends disabling internet-facing RDP if possible, and if not, to limit the number of employees who can access servers over the internet.
Strong passwords must be set for all accounts that can login using RDP and multi-factor authentication should be implemented. Virtual private networks should be set up and used to broker all RDP connections, and external connections to local machines on port 3389 and other RDP ports should be disabled at the perimeter firewall.
Since these attacks often involve disabling security software, passwords should be set to prevent settings from being changed by unauthorized individuals. If any unsupported operating systems are in use, or if patches for known vulnerabilities cannot be applied, those computers should be isolated so they cannot be accessed from the internet via RDP.
ESET has also developed a new detection layer within the ESET Network Attack Protection solution, which now blocks incoming brute force attacks from external IP addresses using RDP and SMB protocols, although the above measures are still required to reduce the risk of an attack.
