A new variant of Emotet spreads like a worm sending copies of itself to computers connected to WiFi networks within range of an infected device. This is the first time that this method of propagating the Emotet Trojan has been identified, but it would appear that it is not actually new and has been used for many months.
The new Emotet capability was detected by researchers at Binary Defense on January 23, 2019. Their research suggests this method of delivery has gone undetected for almost two years. The binary they identified has a timestamp of 04/16/2018.
The researchers at Binary Defense have been analyzing new strains of Emotet almost daily since the campaigns started again in August 2019 after a period of inactivity, but they failed to identify the Wi-Fi spreading behavior until last month. They suggest this may be due to the module not activating the WiFi spreading behavior on VMs and in sandboxes without a Wi-Fi card.
Emotet is already one of the most prevalent and dangerous malware threats. Emotet already uses a variety of techniques to propagate, including sending copies of itself via email from an infected device and through infected networks. This new method of spreading the Emotet Trojan could rapidly increase infections.
The Emotet Trojan is delivered as a self-extracting RAR file that includes two binaries: service.exe and worm.exe, with the latter executing automatically when extracted from the RAR file. The worm.exe binary uses the wlanAPI interface to profile wireless networks within range, and then attempts to brute force those Wi-Fi networks if they are password protected.
If a Wi-Fi network is not password protected, or if the password is successfully brute forced, the worm then searches for other Windows devices with non-hidden shares. Attempts are then made to brute force the password for the Admin account and other users. If successful, the service.exe binary is dropped on the device and a new service is added – Windows Defender System Service – which allows it to gain persistence and the embedded Emotet Trojan is then dropped.
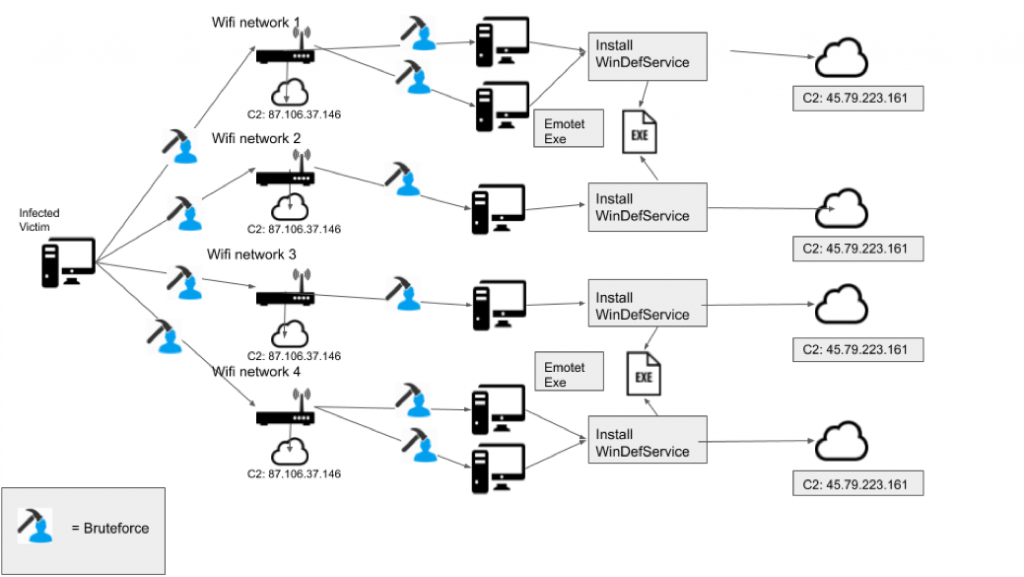
Emotet Propagation via WiFi. Image Source Binary Defense
This recently discovered method of spreading shows how important it is to set strong passwords for WiFi networks to make it harder for the password to be brute forced. “Detection strategies for this threat include active monitoring of endpoints for new services being installed and investigating suspicious services or any processes running from temporary folders and user profile application data folders,” suggest the researchers.
