Payments to resolve ransomware and data exfiltration extortion attacks increased in the first quarter of 2021, with the rise largely due to the Accellion legacy File Transfer Appliance (FTA) cyberattack and attacks by small ransomware groups such as CLoP. CLoP was highly active throughout Q1 and was the 4th most common ransomware variant in Q1, having not even been in the top 10 in Q4, 2020.
Ransom payments declined in the last quarter of 2020, but the fall was short-lived. Coveware’s Quarterly Ransomware Report for Q1 2021 shows the average payment increased by 43% to $220,298 and the median payment rose 59% to $78,398.
The CLoP threat group has been targeting large organizations and demanding very high ransoms to prevent the exposure of data stolen in the attacks. The CLoP ransomware gang was also involved in the attack on the Accellion FTA. Two zero-day vulnerabilities were exploited to achieve remote code execution within the Accellion FTA instances which allowed data exfiltration, although ransomware was not used as it was not possible to deploy the ransomware across victims’ environments. The threat of the exposure of stolen data alone was sufficient to get dozens of victims to pay. While most did not, the CLoP gang still raked in tens of millions of dollars from Accellion FTA attack. Those that did not pay had their data exposed on the CloP data leak site.
The number of ransomware attacks involving data exfiltration increased once again, rising from 70% of attacks in Q4, 2020 to 77% of attacks in Q1, 2021. Threats are issued to expose or sell the stolen data if the ransom is not paid, which has proven to be a successful strategy even though there is no guarantee that stolen data will be deleted when payment is made. The exfiltrated data are often saved to multiple locations can be accessed by third parties, so even if the threat group deletes data, other copies may well exist. Coveware says the number of organizations refusing to pay to prevent a data leak is increasing for these reasons.
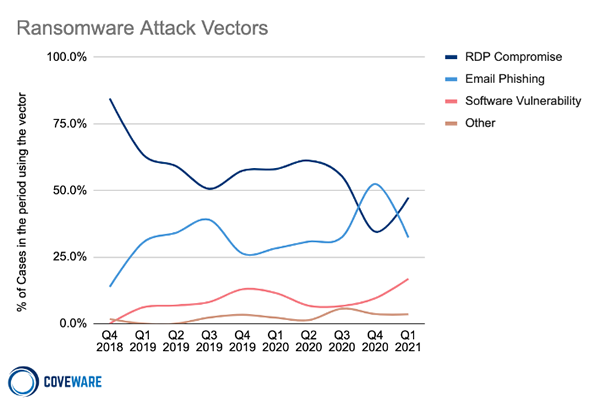
There was a change in ransomware attack vectors in Q1, with Remote Desktop Protocol compromises the top attack vector once again after being overtaken by phishing attacks in Q4, 2020. Phishing attacks are still commonly used to infect computers with credential-stealing malware and remote access Trojans that are used in the first stage of ransomware attacks.
There has also been a steady rise in software compromises since Q3 2020, most commonly in attacks on smaller organizations with under 1,000 employees. Coveware believes the majority of ransomware operations do not exploit software vulnerabilities themselves but pay for access to already compromised systems and partner with hackers who specialize in the exploitation of software vulnerabilities. The most common vulnerabilities exploited in Q1 were flaws in Fortinet and Pulse Secure VPNs.
Exploitation of software vulnerabilities was the main attack vector used by two of the top three ransomware operations – Sodinokibi (REvil) and Lockbit – with phishing the main attack vector used by the Conti ransomware gang – The second most prevalent strain of ransomware.
Coveware identified multiple failures by ransomware operations in Q1, which the company attributes to problems operating criminal enterprises at scale. Egregor ransomware was shut down after only 4 months, NetWalker had its infrastructure taken down by law enforcement, and technical problems were experienced by Sodinokibi, BlackKingdom, and Lockbit, which meant some victims suffered permanent data loss.
Coveware also observed the Lockbit and Conti operations engaging in tactics that hampered victims’ recovery after ransoms were paid, including attempting to steal more data from victims and trying to re-deploy their ransomware to further extort victims. These tactics were rare in 2020 but are becoming more common.
Professional services was the most targeted industry sector accounting for almost a quarter of ransomware attacks in Q1 (24.9%), with law firms increasingly targeted. Healthcare and public services were in joint second with 11.6% of attacks followed by the food & staples sector (8%) and consumer services (7.1%).