Warnings have been issued about ongoing malicious cyber activities by the Advanced Persistent Threat (APT) actor known as APT28/Strontium/Fancy Bear. The APT group has been using a Kubernetes cluster in brute force attacks on the U.S. government and the private sector and has been targeting cloud services including Office 365 in a cyber espionage campaign.
On July 1, 2021, a joint cybersecurity advisory was issued by the National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI) and the UK’s National Cyber Security Centre (NCSC) warning about the ongoing attacks.
APT28 is believed to be part of the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), which has targeted hundreds of U.S. and foreign organizations.
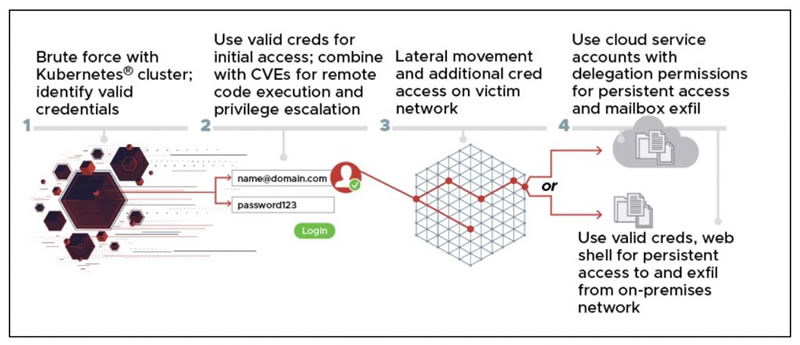
APT28 is using password spraying tactics using previously leaked usernames and passwords, dictionary words, and commonly used passwords to gain access to accounts. Once valid credentials have been identified, the group moves laterally within networks and collects and exfiltrates data of interest. These tactics are nothing new and are used by many malicious threat actors in cyberattacks; however, the use of containers has allowed the APT group to easily scale up its brute force attacks.
The cybersecurity alert explains that once valid credentials are identified, APT28 uses a variety of publicly known exploits to move laterally, including the Microsoft Exchange Server vulnerabilities CVE-2020-1744 and CVE-2020-0688. This allows the threat actor to evade defenses and collect and exfiltrate information in the breached networks, including mailboxes.
The attacks have been conducted since at least mid-2019 and are ongoing. APT28 has conducted attacks on a broad range of targets, with most attacks occurring in the United States and Europe on targets such as government and military, defense contractors, energy companies, higher education, logistics companies, law firms, media companies, political consultants or political parties, and think tanks.
The targets are diverse with different network structures, so a variety of tactics, techniques, and procedures (TTPs) are used in the attacks, 21 of which have been detailed in the cybersecurity alert along with several mitigations that can be implemented to improve defenses.