A new, theoretical cyberattack has been described by a team of researchers at Ben-Gurion University (BGU) in Israel that could be used in a devastating biological attack.
Every year, commercial DNA synthesizers create billions of nucleotides, which are sold to customers and generate billions of dollars in sales. There is growing concern that a cyberattack could be conducted to interfere with the synthetic DNA orders. Just as in a supply chain attack, where malware is inserted into a product that is then shipped out pre-loaded with malware to its customers, a similar type of attack could lead to the DNA of pathogens being synthesized that would encode for harmful proteins and toxins.
The research, which was recently published in the paper – Cyberbiosecurity: Remote DNA Injection Threat in Synthetic Biology – which as recently published in the journal Nature Biotechnology, describes such an attack scenario.
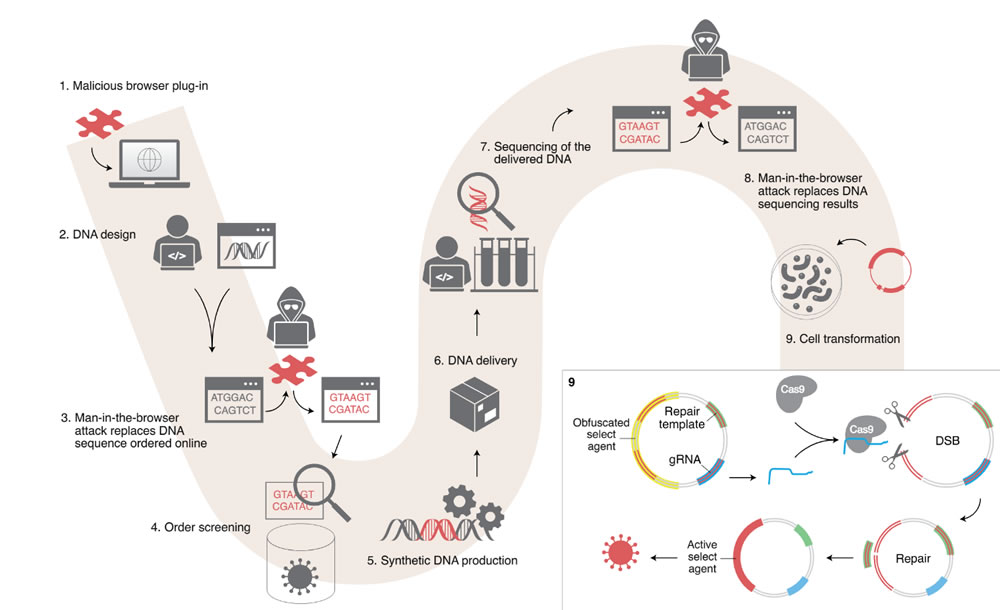
The researchers explain that the process could potentially start with a malicious browser plugin on a researcher’s computer, which could be added using social engineering techniques in a standard spear phishing attack. The browser plugin could be used in a man-in-the-middle attack to replace the DNA sequence which has been ordered online.
Provided that sequence passes the checks put in place by the DNA synthesizer provider, the DNS sequence would go into production and the product would be shipped and delivered. When the harmful sequence is received, the browser plugin could be used to interfere with the sequencing results, and the harmful DNA would then be used, unknowingly by the researcher. That harmful DNA sequence could encode for a dangerous protein or produce a toxin, as shown in the image below.
Image Source: Nature Biotechnology: Malicious elements indicated in red.
Fortunately, conducting such an attack is not straightforward, as DNA synthesis providers do have safety checks in place to check requested DNA against potentially problematic DNA sequences prior to production. For instance, the U.S. Department of Health and Human Services requires screening protocols to be put in place to scan for potentially harmful DNA. The problem is that there is no totally comprehensive database of all pathogenic sequences against which a check can be performed.
The researchers note that there are weaknesses in the Screening Framework Guidance for Providers of Synthetic Double-Stranded DNA and Harmonized Screening Protocol v2.0 systems which could be circumvented in such an attack. The researchers demonstrated that by using obfuscation, 16 out of 50 DNA samples were not detected by these screening systems.
In such a scenario, an attacker would not need to have access the biological agent itself at any point in the attack process, as researchers and scientists could be duped into making and using the pathogenic sequence in what the Israeli researchers describe as an “end-to-end cyberbiological attack.”
There is considerable research currently being conducted into the CRISPR-Cas9 in vivo gene editing system. This system is used to make changes to the DNA to remove harmful mutations and correct defective genes in the lab, but now in clinical trials on humans. By altering the system to make edits in the wrong place there could be grave repercussions.
“This attack scenario underscores the need to harden the synthetic DNA supply chain with protections against cyber-biological threats,” said Rami Puzis, head of the BGU Complex Networks Analysis. “To address these threats, we propose an improved screening algorithm that takes into account in vivo gene editing.”