The U.S. Department of Homeland Security Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert about an ongoing phishing campaign against government agencies that is attempting to obtain credentials for Small Business Administration COVID-19 loan relief accounts.
The campaign uses a spoofed version of the SBA COVID-19 relief webpage to obtain credentials, with links to the fraudulent website distributed through phishing emails. The campaign started in April, with a further wave of emails detected in late July, with the campaign continuing in August. Phishing emails have been sent to Federal Civilian Executive Branch, as well as state, local, tribal, and territorial government organizations.
There appears to be two main goals of the attackers. Emails have been sent directing recipients to the fake SBA website to obtain credentials, while others have been used to deliver GuLoader malware. The latter is used to download a variety of malicious payloads. Both sets of phishing emails have been sent from the same spoofed email address.
The GuLoader emails have an attachment named SBA_Disaster_Application_confirmation_Document_COVID-Relief.img. While this appears to be an image file, it actually has a double extension and is an executable file (.exe). On Windows devices, known file extensions are hidden by default, so the .exe part of the file name will be hidden. These emails use a variety of subject lines such as “SBA Grant/Testing Centre Vouchers” and “Coronavirus Pandemic Loan (COVID-19),” according to Malwarebytes.
The phishing emails detected by CISA use the subject line – SBA Application – Review and Proceed – and the sender of the emails is spoofed and appears to be disastercustomerservice@sba[.]gov.
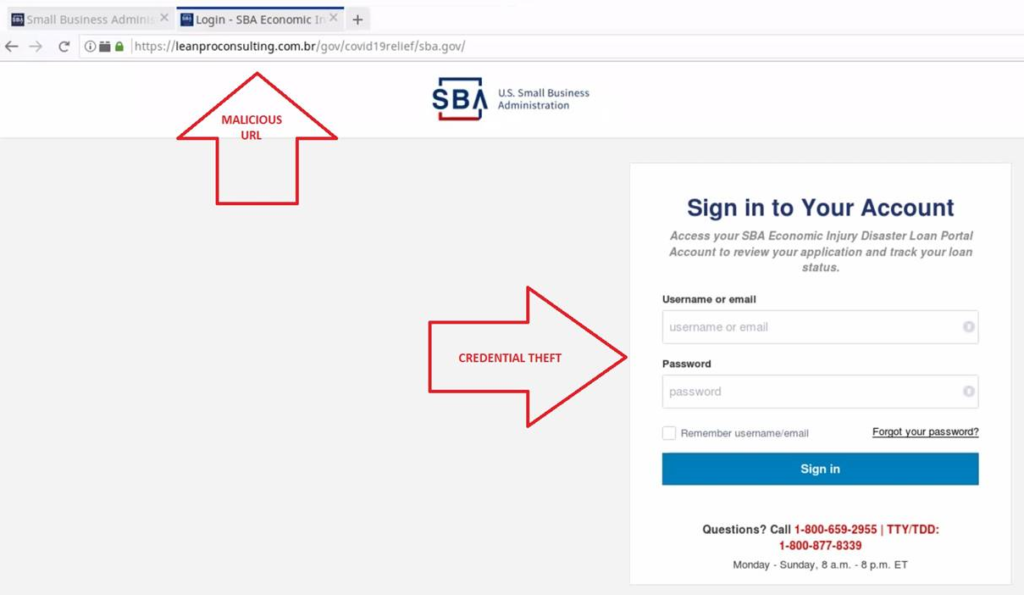
Multiple URLs have been used in this campaign, some of which use a .br TLD, including hxxps://leanproconsulting[.]com.br/gov/covid19relief/sba.gov
The above URL and others used in the campaign to phish for credentials spoof the SBA account login page, as detailed in the image below:
CISA has published a list of confirmed IoCs and offers mitigations that can be implemented to strengthen organizations’ security posture. You can view the IoCs and mitigations here.