Many organizations struggle with vulnerability management due to the number and complexity of new resources and limited resources to devote to remediating vulnerabilities. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently issued guidance to help organizations improve vulnerability management by implementing an efficient process for assessing and remediating vulnerabilities.
Large organizations generally have mature vulnerability management programs, but even these organizations are always looking to make vulnerability management more efficient, so they too can benefit from the guidance; however, the guidance will be of greatest use to smaller organizations, which often do not know where to start when it comes to managing vulnerabilities and how they should allocate their resources.
It is unlikely to be possible to remediate all vulnerabilities immediately and doing so is not the best use of time and resources. The number of vulnerabilities now being discovered continues to grow, yet estimates suggest that only around 15% of disclosed vulnerabilities are actually exploitable. Attempting to patch all vulnerabilities promptly is inefficient. Vulnerabilities need to be assessed, the risk of exploitation determined, and then patching needs to be prioritized accordingly, with the critical, actively exploited, and most dangerous vulnerabilities remediated first.
CISA has been working on improving the vulnerability management ecosystem, and along with its partners has identified three steps that are critical. In a recent blog post, Eric Goldstein, Executive Assistant Director for Cybersecurity at CISA, explained those steps:
- To introduce greater automation, including expanding the use of the Common Security Advisory Framework (CSAF).
- It must be made easier for organizations to understand whether a given product is impacted by a vulnerability through the widespread adoption of Vulnerability Exploitability eXchange (VEX)
- CISA must help organizations more effectively prioritize vulnerability management resources through the use of Stakeholder Specific Vulnerability Categorization (SSVC), including prioritizing vulnerabilities on CISA’s Known Exploited Vulnerabilities (KEV) catalog.
SSVC is a decision-making tree that was developed by CISA and the Software Engineering Institute (SEI) at Carnegie Mellon University for use by the federal government and critical infrastructure organizations for assessing vulnerabilities and prioritizing the response. The SVCC can be used to categorize vulnerabilities and assign them to one of four categories, based on the exploitation status, technical impact, whether the vulnerability is automatable, mission prevalence, and the public well-being impact. The four categories are:
- Track – Immediate action not required – Patch within standard timeframes
- Track* – Immediate action not required, but closer monitoring is required for any changes – Patch within standard timeframes
- Attend – Attention required from internal supervisory-level individuals – Patch sooner than standard timeframes
- Act – Attention required from internal supervisory-level and leadership-level individuals – Patch as soon as possible
Organizations can use the CISA decision tree calculator to determine the category for each vulnerability:
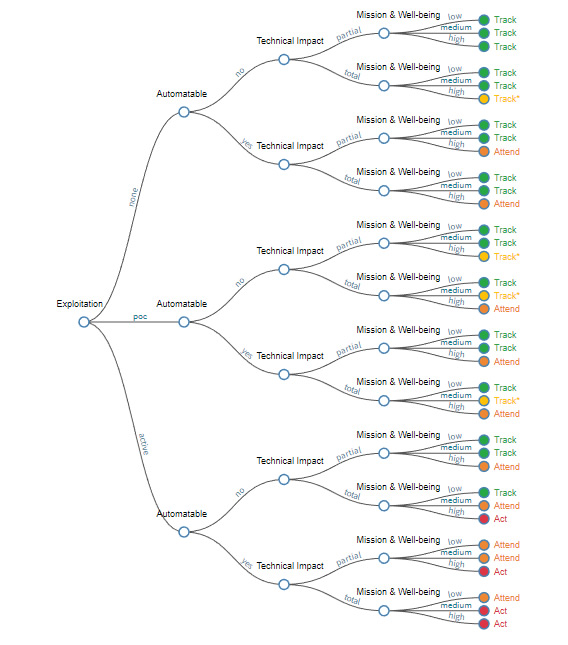
CISA SVCC Decision Tree Calculator
The SVCC should be used in conjunction with the Known Exploited Vulnerabilities (KEV) catalog, Vulnerability Exploitability eXchange (VEX), and the Common Security Advisory Framework (CSAF). Guidance on the SVCC is available here (PDF).
