Security researchers at Trend Micro have identified a new remote access Trojan (RAT) dubbed BIOPASS, which uses legitimate live streaming software to provide the attackers with a real time view of the victim’s computer screen and stream audio from the affected device. This is achieved by downloading and using either FFmpeg and Open Broadcaster Software.
There have been many sextortion scams conducted over the past couple of years where attackers claim to have recorded audio and video of the user viewing adult material. In those scams, no recording exists; however, BIOPASSS could provide attacker with such recordings.
Using either FFmpeg or Open Broadcaster Software, the attackers would be able to monitor an infected system, with audio and video streams sent to the cloud and accessed via the BIOPASS control panel. The researchers also note that the malware enumerates installation folders of messaging applications such as WeChat, QQ, and Aliwangwang.
BIOPASS malware is capable of exfiltrating data from the victim’s device, including login information and cookies from a range of internet browsers. A Python Plugin was also identified that is capable of stealing chat histories from WeChat messenger, although it had not been implemented in the version analyzed by the researchers.
The malware is being used in attacks in China, with the researchers distributing BIOPASS malware via Chinese gambling websites that have been compromised. When visitors land on the compromised website, JavaScript serves the malware installer via a fake Adobe Flash Player and Microsoft Silverlight downloader. A security warning is displayed instructing the visitor to download one of the installers. That installer loads either the BIOPASS RAT or Cobalt Strike shellcode.
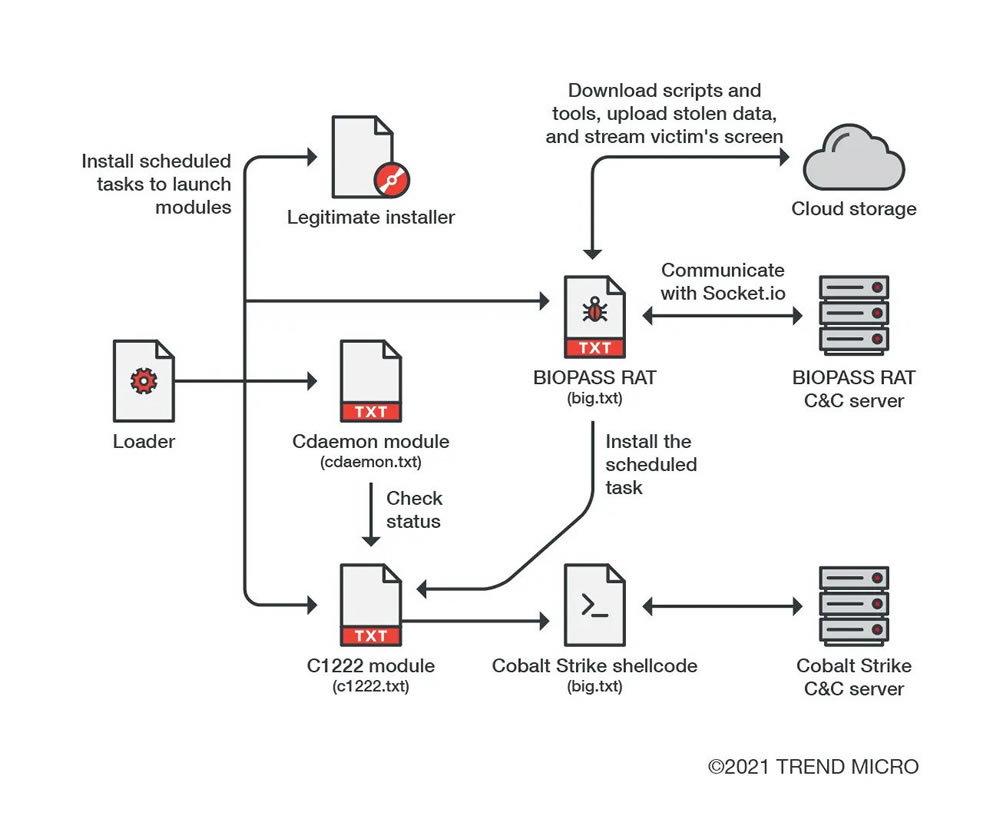
Source: Trend Micro
Legitimate installers for Flash Player and Silverlight are also provided on the site, which download the legitimate program installers from their Alibaba cloud storage account or the official download websites.
The Trend Micro researchers were unable to attribute the malware to a threat group, although they did identify some links to the Chinese hacking group APT41 (Winnti).
