Researchers at Eclypsium have identified four serious vulnerabilities in the BIOSConnect feature of Dell SupportAssist that could be remotely exploited by attackers to gain full control of targeted devices. The flaws are present in an update mechanism that affects 129 models of enterprise and consumer laptop and desktop computers protected by Secure Boot – Around 30 million devices.
Secure Boot is a security feature that ensures devices can only be booted using software trusted by the device original equipment manufacturer (OEM). The flaws mean the protections of Secure Boot can be circumvented, which would allow an attacker to take control of the boot processes on vulnerable devices. By exploiting the vulnerabilities an attacker would also be able to subvert the operating system and higher level security controls.
Dell SupportAssist comes pre-installed on the majority of Windows Dell machines, with the BIOSConnect feature used to update the firmware of the devices and to perform remote OS recoveries. The feature helps users of Dell devices ensure the firmware is kept up to date, and while this has a clear security advantage, vulnerabilities in these automatic update features can have the opposite effect.
In this case, the vulnerabilities allow a remote attacker to exploit the UEFI firmware of a host and gain full control of the device with high-level privileges. That would make the vulnerabilities an attractive target for attackers.
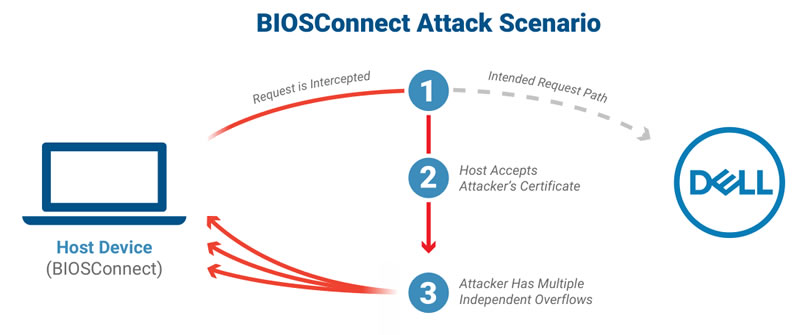
The vulnerabilities have a cumulative CVSS severity score of 8.3 out of 10. The first vulnerability – CVE-2021-21571 – is due to an insecure TLS connection from the BIOS to Dell. When BIOSConnect attempts to connect to Dell’s backend HTTP server for a remote update, the system’s BIOS connects to Dell’s backend services over the Internet. The TLS connection accepts any valid wildcard certificate, so an attacker with a privileged network position could intercept the communication, impersonate Dell, and deliver their own content to the targeted device.
Any of three overflow vulnerabilities could then be exploited – CVE-2021-21572, CVE-2021-21573, and CVE-2021-21574 – all of which could individually lead to pre-boot arbitrary code execution in the BIOS. Two of the vulnerabilities affect the OS recovery process, with the other affecting the firmware update process.
Source: Eclypsium
Dell has already addressed two of the flaws in a May 28, 2021 update, but CVE-2021-21571 and CVE-2021-21572 will need to be corrected by updating the system BIOS/UEFI. The researchers recommend not using BIOSConnect to apply BIOS updates. “It is advisable to run the BIOS update executable from the OS after manually checking the hashes against those published by Dell,” said Eclypsium.
If it is not possible to apply the updates immediately, Eclypsium recommends disabling BIOSConnect. This can be done from the BIOS setup page or by using the Dell Command | Configure (DCC) Remote System Management tool.
