Password salting and password peppering are two methods of preventing hashed passwords from being deciphered by hackers using brute force techniques or rainbow tables. Unfortunately, users rarely know whether online vendors are salting or peppering passwords, so businesses and individuals still need to take responsibility for protecting online accounts using other methods.
In a previous article, we discussed password hashing and explained what it was, how it was meant to protect databases of passwords, and why it doesn’t. To summarize, when you create an online account, many websites convert your plain text password into a string of letters and numbers and save the string rather than the password to prevent passwords from being exposed in a data breach.
However, because so many people use the same password for multiple accounts, hackers are now able to reverse engineer the most commonly-used hashing algorithms and decipher hashed passwords – rendering the hashing process ineffective when used on its own. For this reason, many online websites now supplement hashing processes with password salting and password peppering.
What is Password Salting?
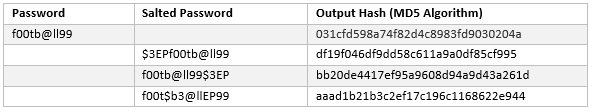
Password salts are a set of characters that are automatically added to – or included in – a user´s password before it is hashed, resulting in a completely different hashed output. For example, when the password “f00tb@ll99” is hashed using the MD5 hashing algorithm, it produces the output 031cfd598a74f82d4c8983fd9030204a. By adding any characters (i.e., $3EP), you get a completely different output which, if reversed engineered would not reveal the user´s real password.
The user is not responsible for entering additional characters – it is done automatically – and the additional characters can be added at the beginning of the password, at the end, or scattered throughout. However, password salting does not prevent weak passwords being deciphered. Using the example above, if a hacker were to reverse engineer the salted output with the salt at the beginning or end of the password, it would not be difficult to figure out that the salt is $3EP and the user´s password is f00tb@ll99.
What is Password Peppering?
Password salting and password peppering are similar techniques inasmuch as they both add characters to a user’s password before hashing the password. However, with password salting, the salt (i.e., $3EP) is stored by the website so it knows what characters to add to the user’s password before hashing it to ensure the hashed output matches the one stored in the password database.
With password peppering, characters are added to the password when an account is created, and the hashed output is stored in the password database. However, the added characters are not stored by the website; and, when a user logs in, the website has to run each combination of the password plus pepper until the hashed output matches the one stored in the password database.
The advantage of peppering over salting is that, if a hacker attempts to extract password data from a database, it is going to take hundreds of times longer to connect peppered hashes with plain text passwords depending on the number of characters in the pepper and the complexity of the password. In most cases, the extra effort will not be worth it to the hacker.
Is Password Salting and Password Peppering Enough to Protect Online Accounts?
While password salting and password peppering are usually enough to prevent complex passwords from being deciphered once extracted from an online database, it doesn’t prevent the website database from being hacked and any un-salted or un-peppered data from being extracted (i.e., credit card numbers). It may also be the case with password salting that the salt and its location are revealed.
Furthermore, it is difficult to know which websites are using password salting and password peppering. Many websites (incorrectly) rely solely on password hashing to prevent passwords from being deciphered in the event of a data breach – while thousands don’t even hash passwords and maintain databases of plain text passwords. These websites are best avoided.
Therefore, to maximize the protection of online accounts, individuals and businesses are advised to add secondary authentication methods such as two-step login – preferably with hardware devices like YubiKeys. which are not susceptible to man-in-the-middle attacks such as SIM swaps and SS7 interceptions, and which mitigate the inconvenience of two-step login due to their ease of use.